This post is authored by Jaime Filson and Dave Liebenberg.
Background

|
| A mosaic made up of 1-800 tech support scam websites |
The amount of fraudulent actors masquerading as legitimate tech support has been on the rise since 2008. According to David Finn, executive director at the Microsoft Cybercrime Center, tech support scammers have made nearly $1.5 billion off of 3.3 million unwitting victims just this year. These scammers typically convince the victim into allowing them access to his/her computer through remote control applications such as TeamViewer. They then present benign processes as malicious, or at times even spread malware themselves. Afterwards, they charge hundreds of dollars for the service.
There are several avenues through which these scammers reach their victims. One of the most insidious are pop-ups and websites asserting that the user's computer is riddled with viruses, and that the only way to fix the problem is to call a provided tech support number.
Talos has been monitoring the incessant creation of these fake tech support websites in order to better understand the way in which these scams operate. We decided to call a company ourselves for some reverse social engineering. Our experiment provided some interesting insights into the methods these scammers use to fool their victims as well as the infrastructure supporting their operations. In addition, we discovered a broad New Delhi-based scamming network employing multiple websites and VOIP phone numbers to carry out their duplicitous activities.
The Call
Talos has been scouring the web for newly created domains belonging to fraudulent tech support companies. These websites claim that viruses have been detected on a user's computer necessitating a call to a listed tech support number. We came across one such website at macinscan[.]org, which displayed a "Safari system warning" urging users to call 1-855-720-2636 to address an issue with their Macs.
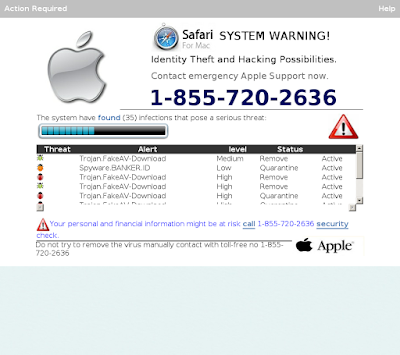
In order to analyze the scammer's activities, we set up a dedicated virtual machine and had an analyst feigning a low level of technical proficiency call the number. We made sure to record both the audio of the phone call as well as the screen of the virtual machine (The full video and audio can be found in the links below).
A woman answered the phone and introduced herself as "Kelly Thompson" in accented English. We described to her how we encountered the error message. She asserted that she could help take care of the issue, even after we affirmed that our computer was, in fact, a Toshiba and not a Macbook.
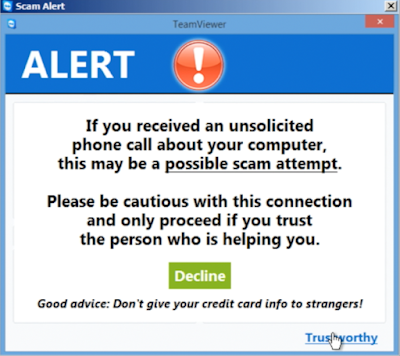
Kelly then instructed us to visit a website with a URL shortened by TinyURL. This website downloaded TeamViewer, through which they exercised remote control of our computer, a common tactic used by these types of scammers. Although TeamViewer sent us an alert that people could take advantage of the software for fraudulent purposes, Kelly promptly instructed us to ignore this warning.
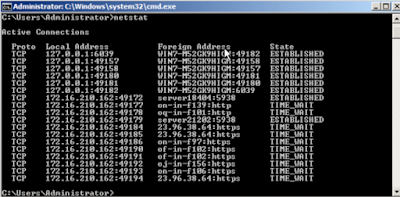
Now enjoying remote access to our computer, Kelly displayed a variety of harmless processes that she presented as evidence of viruses and malicious activities. For example, she opened up the command line and displayed the network connections, claiming that the foreign addresses represented hackers that were infiltrating our system from another country.
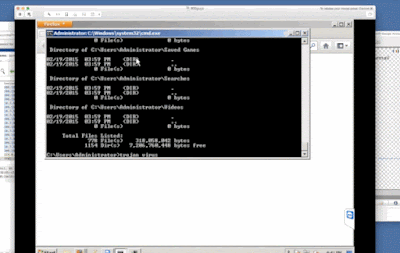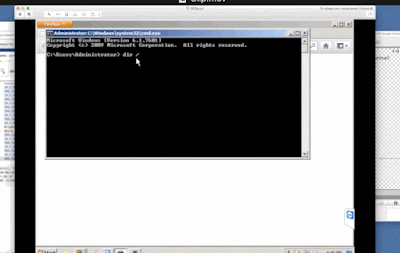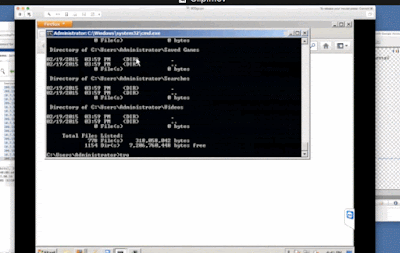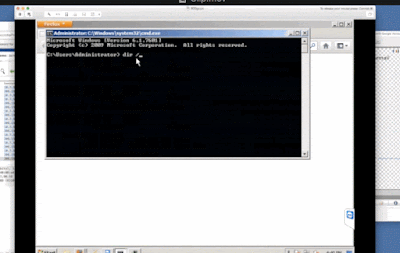
Next Kelly opened up a command prompt and recursively listed all the directories and files in the administrator directory, although she claimed this was actually a security scan looking for malware. At the end of the lengthy list, she actually typed the words "Trojan Virus," which she presented as evidence that she had discovered a Trojan on our computer.
After taking us to a Wikipedia page on Trojans so that we fully understood the nature of the problem, she said that her team would clean our computer and then call us back. She said they would charge us $100 for the removal of the Trojan virus and $50 to fix our security drivers. We explained we could only pay by check and Kelly then handed us off to a person in charge of billing, who she identified as Alex. Alex then instructed us to make a check out to the following:
Essential Services Worldwide
4630 Border Village Road Suite N1497
San Ysidro, CA, 92173
We hung up and watched as a scammer, who TeamViewer identified as Denzil, changed various settings on the PC and downloaded a variety of programs and browser extensions intended to enhance security settings. You can find the recording of the whole session below.
Kelly called back the next day to ask for our check number and email address and inquired if we were happy with their services. She then offered us a warranty on the computer for the low price of $120/year.
Tracking the Scammers
After confirming the deceitful nature of the scam through our phone call, we decided to find out more information about the people behind the operation. Luckily, they provided us an excellent entryway with their payment instructions.
The name of the company they told us to make the check out to, Essential Services Worldwide, matches an LLC based in Wilmington, Delaware. Their Yellowpages listing provides a company website, onlyforsupport[.]com, which offers remote tech support and also employs the TeamViewer software. The IP for this website, 162.144.91.150, resolves to a number of other domains offering similar type services for AOL, Hotmail, and PCs. At least one of these websites was also found to host a malicious executable. freepccleandownload[.]com is one site that was found hosting a PE that is detected as adware by 17/55 AV engines on VirusTotal.
Another domain that resolves to this IP is essentialservices[.]in. This is the website for Essential Services Outsource Pvt Ltd, a hiring and recruitment company based in New Delhi specializing in "Desktop Support, Telemarketing, Email Marketing, SMS Marketing, Internet Marketing, and SEO." The website appears to be a core piece of infrastructure supporting the other components of the scam. Through job postings on the site, it is clear that Essential Services recruits telemarketers who disguise themselves as tech support for the other websites resolving to that IP.
According to corporatdir.com, the man behind essentialservices[.]in appears to be Sharad Goel. He is listed as the registrant of the website as well as a managing director for the company. In addition, his name is attached, via his username sharadmcp2003, to most of the recruitment posts on the website. Furthermore, Sharad Goel or essentialservices[.]in is named as the registrant for several of the other domains resolving to 162.144.91.150.
Digging a bit more, we found a mouthshut.com profile for Sharad Goel who appears to be 32 and based in New Dehli. We also found a LinkedIn profile for Sharad and it appears he was educated at St. Mary's Sr. Sec. School in Uttarakhand. His work experience includes sales and telemarketing in SecPoint, a Danish IT and security company. He has been director of Essential Services since 2011 and works in another recruitment outfit as well called SMS Consultancy.

|
| Sharad Goel (Taken from his Google+ page) |
To sum up so far, it would appear Sharad Goel and a number of tech support websites under his control through Essential Services are linked to our original macinscan[.]org scammer through their payment instructions. There were other connections as well.
According to WHOIS data, macinscan[.]org -- the original website we contacted -- is registered to Farman Anees, located in New Dehli with phone number 91-9910282896 and email farman.anees2@gmail.com. A LinkedIn page for Farman Anees lists him as an HR manager for Essential Services since February 2015. In addition, a post recruiting for a technical support position at Essential Services on Indian networking site beBee lists his email and phone number for points of contact.
Farman Anees appears to be in Sharad Goel's "trusted circle" on Google+ page. According to Anees' profile on that site, he graduated from St. Xavier high school in Delhi in 2009, making him around 24. According to his LinkedIn profile he then attended the Chhotu Ram Rural Institute Of Technology. The tagline for his Google+ profile reads "genius by birth, evil by choice."
After establishing the New Delhi-based infrastructure of the scam, we also identified a U.S.-based individual who appears to act as money handler for the operation.
The U.S. Money Handler
A search of the payment address that macinscan[.]org directed us to—4630 Border Village Road Suite N1497, San Ysidro, CA, 92173—matches a WHOIS registrant address for the website tesserboigltd[.]com. The registrant's name is Sergio I. Cortes Jr., his email sicortesjr@gmail.com, and his organization is called "Tesser Enterprises."
Fortunately for us, Sergio I. Cortes Jr. has a relatively large social media footprint, including a LinkedIn, Badoo profile, YouTube page, and a profile on a freelancer website. Through these various profiles, we can gather that he attended Grossmont College from 1990 to 1993 and San Diego State University from 1993-1995. He also claims to have served as an interim accountant at Blueways USA, which designs and builds hybrid electric drive systems and components. According to a post on a car enthusiast forum, he also served at one point in time as a loan officer. He was also quoted in a press release for communication software Intellinote as president of Tesserboig Ltd.
Both Sharad Goel and Sergio I. Cortes Jr. appear to have been frequent users of freelancer.com in the past. In one post Talos found, Sergio claims he has experience in accounting, finance, law, and management as well as providing SEO services. Per Sergio's profile, he also claims to be fluent in French, Italian, Portuguese, and Spanish. In another post, Talos was able to locate a job posted by Sharad Goel looking for a "virtual bank account in the USA" to allow him to withdraw funds into the account and later wire them back to India. Sergio I. Cortes Jr. appears to be one of two top bidders on the project.

|
| Sergio I. Cortes Jr.'s Taken from his LinkedIn profile |
There are other indications of Sergio I. Cortes Jr.'s connection to the Essential Services crew. One of the domains resolving to the same IP as the other fake tech support websites is bulkwhatsapp[.]org, a WhatsApp spamming service (that also employs a TeamViewer demo). The website instructs purchasers to send wire transfers to a Citibank account registered to "Tesser Enterprises" and provides the following details:
Tesser Enterprises, Citibank, 322271724, Account Number, 205862568, address: 352 H Street Chula Vista, CA 01910
In addition, sicortesjr@hotmail.com is listed as a PayPal address.
Actions Taken
Talos has reached out to Onvoy, parent company of VOIP operator 360 Networks USA, which in turn owns the tech support number we called, in order to get the number shut down.
We have also contacted TeamViewer alerting them of the abuse and reporting the ID used by the Essential Services crew. We also shared the log files from our VM.
Finally, in 2012 the FTC successfully prosecuted several fake tech support companies for violation of the FTC act, which bars "unfair and deceptive commercial practices." We have submitted a complaint and also urge any affected to notify the FTC here:
https://www.ftccomplaintassistant.gov/#crnt&panel1-1
Fake tech support companies are continuing to build websites that frighten susceptible people into employing their useless and potentially harmful services. We encourage everyone to remain vigilant. For its part, Talos will continue to track and report these scammers.
Acknowledgments
We would like to thank Kurt Wismer (@imaguid) for his help in informing us how to look up the owners of toll free numbers.
Appendix A
Full list of domains we found resolving to this IP:
bulkwhatsapp.org
www.onlyforsupport.com
www.techvisitz.com
solutionfortech.com
www.aolhelpline.com
hotmailhelpline.com
essentialservices.in
directmerchant.org
tourstravel.in
onlyforcomputers.com
dialawhisky.com
gurtekcomputer.com
onlyforsupport.com
freepccleandownload.com
getahelp.org
eserviceswllc.com
buytechcalls.com
rkgoel.in
solution4tech.com.
Here is the list of indicators as an attachment.
