It is no longer enough for ransomware actors to encrypt targets’ files, ask for money, and get out.
Over the past several years, these groups are increasingly relying on “double extortion” tactics to try and coax their victims into paying the requested ransom, or else they will leak stolen data to the internet.
In double extortion ransomware attacks, actors perform traditional ransomware actions of encrypting files and folders on a target’s machine. They leave behind a ransom note asking for a certain amount of money, in exchange for a decryption key that can return the target’s network and hardware back to normal working order.
Of course, there is never any guarantee that this decryption key will work appropriately, so Talos recommends several other ransomware mitigation methods to ensure backups are in place to help an organization recover quickly if they are hit with a ransomware attack.
Actors who use double extortion take this a step further, threatening to leak the target’s data to the public and on the dark web if the ransom is not paid. For some organizations, this puts troves of potentially sensitive data at risk of becoming public information, such as personally identifiable information (PII) or financial information that other bad actors may use in follow-on attacks or to steal someone’s identity.
What is the end goal of double extortion attacks?
Ransomware actors hope that by adding on the extra layer of pressure, it makes victims more likely to pay the requested ransom rather than trying to recover on their own.
Any data leaks could lead to legal troubles for the targeted organization, poor public relations and a loss of customer trust.
At the end of the day, ransomware groups are motivated by money. They will do whatever they can to make it more likely for the victim to pay up.
These groups are also increasingly embracing communication with victims to potentially negotiate payment and provide additional pressure on o the victim. Nick Biasini, the head of Talos Outreach, recently discussed these tactics in an episode of Talos Takes, where he summed up ransomware groups’ motivations by saying, “You can’t get a payday if you can’t start a conversation...once they have communication, they know they have a victim who’s potentially ready to play ball.”
Notable example: RA Group
RA Group, a new ransomware actor Cisco Talos recently discovered, explicitly uses double extortion tactics. It runs an actor-controlled website where it posts a list of possible victims and publicly threatens to publish the data it steals from targets.
RA Group claims to include the organization’s name, a list of stolen data and the file sizes of the data it stole and the URL of the website belonging to the victim organization. The ransom notes the actor leaves behind are customized for the victim and are told they have three days to pay the requested ransom or they risk all the stolen data being made public.
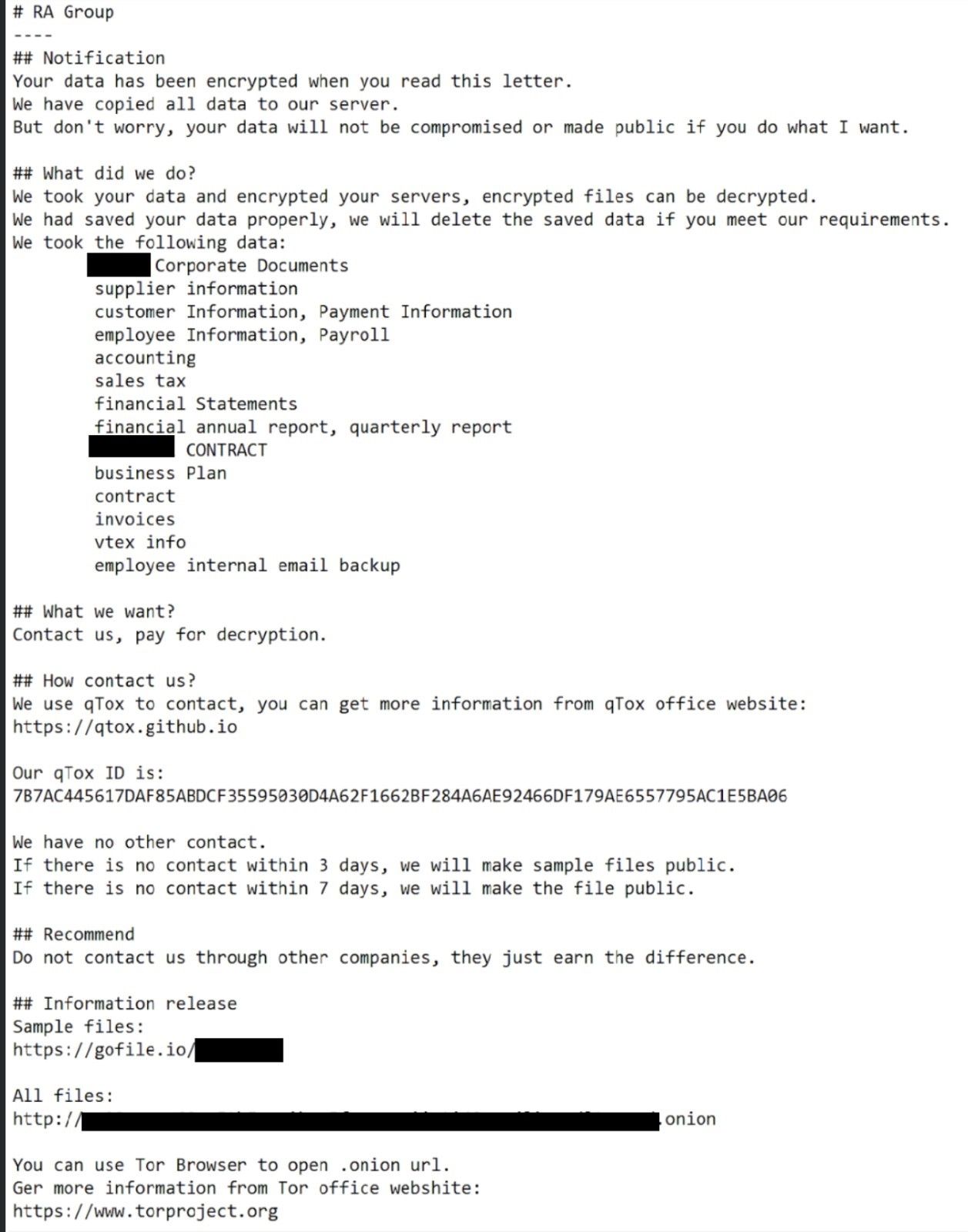
When the three-day mark is reached, RA Group says it will publish “sample files” to prove the legitimacy of its claims. The leak site states that “we will publish documents regularly and all documents will be released within one year.”
RA Group also introduces a new wrinkle to double extortion attacks: the threat that it will sell the data on the dark web. Double extortion tactics are known for leaking stolen data, but the sale is a potentially new gambit.
The group’s leak site is one of the first examples Talos has seen where it publicly threatens to sell the data to other bad actors during that one-year window. It explicitly tells anyone interested in purchasing the data to contact RA Group via qTox, an encrypted instant messaging platform.
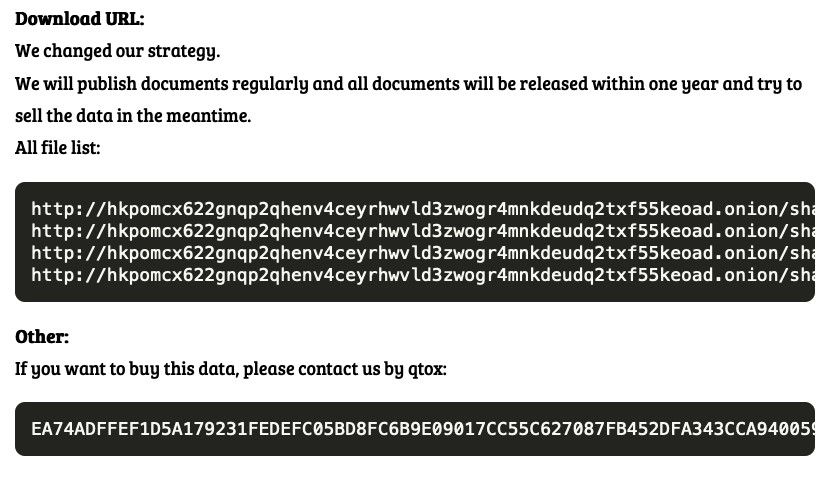
This is potentially a new development in the ransomware landscape and a new way for threat actors to generate revenue from a successful attack.
Talos has researched several other threat actors who started using double extortion methods over the past three years, including UNC2447, Vice Society and Silence Group.
Prevention
To defend against double-extortion ransomware attacks, users and organizations should follow the classic advice for avoiding ransomware:
- Using multi-factor authentication protocols such as Cisco Duo can prevent credential stealing, which often provides threat actors with an initial foothold on the targeted system.
- Cisco Secure Endpoint and other Cisco Secure offerings provide many layers of protection to make any network more resilient. Cisco Secure and Talos have multiple engines, such as Snort, to detect and prevent initial infection, reconnaissance, lateral movement and file encryption.
- Incident Response playbooks and plans can help all organizations prepare for a ransomware attack and outlines steps to take in the event of an attack. Cisco Talos Incident Response can assist in the creation and updating of these documents.
- Perform frequent backups of all systems and important files, and verify those backups are stored in a secure, yet accessible, place. Targets of ransomware can restore operations quickly by restoring from a previous state using backups.
- Provide cybersecurity training to all employees and users to ensure they’re aware of the dangers of various social engineering tactics and common attack vectors for threat actors.
- For additional advice and information, refer to the U.S. Cybersecurity and Infrastructure Security Agency’s (CISA) Stop Ransomware website.