Transparent Tribe APT expands its Windows malware arsenal
Transparent Tribe, also known as APT36 and Mythic Leopard, continues to create fake domains mimicking legitimate military and defense organizations as a core component of their operations. Cisco Talos’ previous research has mainly linked this group to CrimsonRAT, but new campaign
ObliqueRAT returns with new campaign using hijacked websites
By Asheer Malhotra. * Cisco Talos has observed another malware campaign that utilizes malicious Microsoft Office documents (maldocs) to spread the remote access trojan (RAT) ObliqueRAT. * This campaign targets organizations in South Asia. * ObliqueRAT has been linked to th
CRAT wants to plunder your endpoints
* Cisco Talos has observed a new version of a remote access trojan (RAT) family known as CRAT. * Apart from the prebuilt RAT capabilities, the malware can download and deploy additional malicious plugins on the infected endpoint. * One of the plugins is a ransomware known as &
IndigoDrop spreads via military-themed lures to deliver Cobalt Strike
By Asheer Malhotra. * Cisco Talos has observed a malware campaign that utilizes military-themed malicious Microsoft Office documents (maldocs) to spread Cobalt Strike beacons containing full-fledged RAT capabilities. * These maldocs use malicious macros to deliver a multist
Upgraded Aggah malspam campaign delivers multiple RATs
By Asheer Malhotra * Cisco Talos has observed an upgraded version of a malspam campaign known to distribute multiple remote access trojans (RATs). * The infection chain utilized in the attacks is highly modularized. * The attackers utilize publicly available infrastructure s
ObliqueRAT: New RAT hits victims' endpoints via malicious documents
By Asheer Malhotra. * Cisco Talos has observed a malware campaign that utilizes malicious Microsoft Office documents (maldocs) to spread a remote access trojan (RAT) we’re calling “ObliqueRAT.” * These maldocs use malicious macros to deliver the second stage RAT payload. *
Vulnerability Spotlight: Two buffer overflow vulnerabilities in OpenCV
Dave McDaniel of Cisco Talos discovered these vulnerabilities. Cisco Talos recently discovered two buffer overflow vulnerabilities in the OpenCV libraries. An attacker could potentially exploit these bugs to cause heap corruptions and potentially code execution. Intel Research o
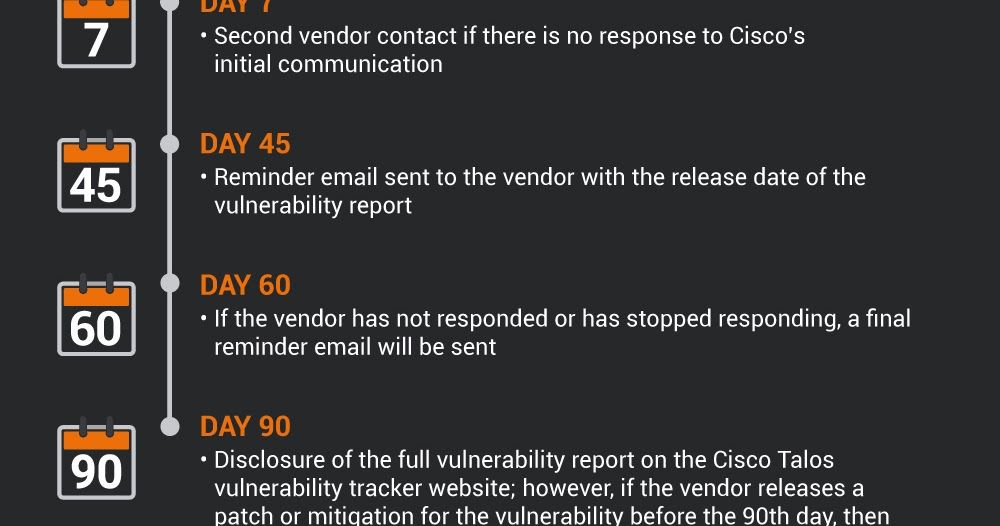
Talos Vulnerability Discovery Year in Review — 2019
By Martin Zeiser. Cisco Talos' Systems Security Research Team investigates software, operating system, IoT and ICS vulnerabilities to make sure we find vulnerabilities before the bad guys do. We provide this information to the affected vendors so that they can create patche