Vulnerability Spotlight: LibTIFF Issues Lead To Code Execution
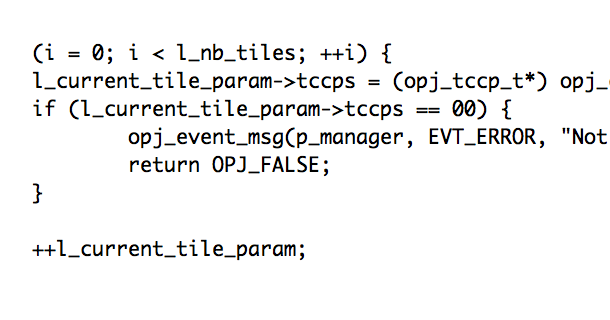
These Vulnerabilities were discovered by Tyler Bohan of Cisco Talos. Talos is releasing multiple vulnerabilities (TALOS-2016-0187, TALOS-2016-0190 & TALOS-2016-0205) in the LibTIFF library . One vulnerability (TALOS-2016-0187) is an exploitable heap based buffer overflow tha
Vulnerability Spotlight: Apple Remote Code Execution With Image Files
Vulnerabilities discovered by Tyler Bohan of Cisco Talos. Many of the wide variety of file formats are designed for specialized uses within specific industries. Apple offers APIs as interfaces to provide a definitive way to access image data for multiple image formats on the App
Vulnerability Spotlight: Local Code Execution via the Intel HD Graphics Windows Kernel Driver
This vulnerability was discovered by Piotr Bania. Talos, in coordination with Intel, is disclosing the discovery of TALOS-2016-0087, a local arbitrary code execution vulnerability within the Intel HD Graphics Windows Kernel Driver. This vulnerability exists in the communication
Vulnerability Spotlight: Pidgin Vulnerabilities
These vulnerabilities were discovered by Yves Younan. Pidgin is a universal chat client that is used on millions of systems worldwide. The Pidgin chat client enables you to communicate on multiple chat networks simultaneously. Talos has identified multiple vulnerabilities in the
TeslaCrypt: The Battle is Over
Talos has updated its TeslaCrypt decryptor tool, which now works with any version of this variant of ransomware. You can download the decryptor here. When Talos first examined TeslaCrypt version 1.0 in April of 2015, we articulated how this ransomware operated and were able to d
Vulnerability Spotlight: PDFium Vulnerability in Google Chrome Web Browser
This vulnerability was discovered by Aleksandar Nikolic of Cisco Talos. PDFium is the default PDF reader that is included in the Google Chrome web browser. Talos has identified an exploitable heap buffer overflow vulnerability in the Pdfium PDF reader. By simply viewing a PDF do
Research Spotlight: The Resurgence of Qbot
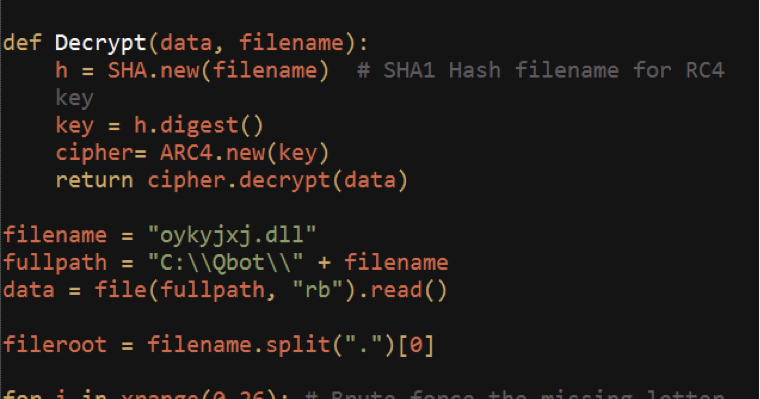
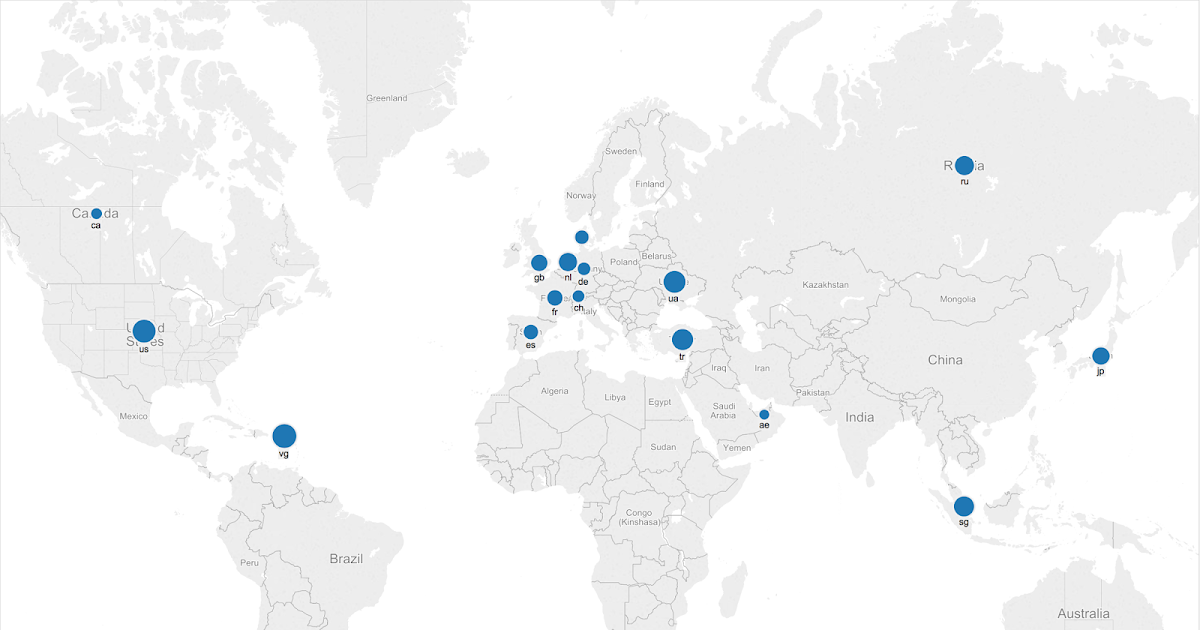
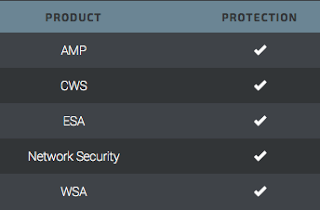
The post was authored by Ben Baker. Qbot, AKA Qakbot, has been around for since at least 2008, but it recently experienced a large surge in development and deployments. Qbot primarily targets sensitive information like banking credentials. Here we are unveiling recent changes to
Tax Scams Gone International
Tax time in the US is quickly approaching. Everyone should be on the lookout for scams that are designed to trick you out of your money and personal information. The IRS is warning users about an increase in the number of email scams being used this year. However, these attacks a
Operation Blockbuster: Coverage for the Lazarus Group
The threat landscape is in constant flux. In many situations, the entire security community must work together to combat some of today’s larger threats. Novetta researched a group of malware families that all appear to be related to the same group of threat actors dubbed “The Laz