TalosIntelligence.com is rolling out a new dispute system
At Cisco Talos, we need customers to be able to provide feedback at all times, whether it be about false positives, false negatives, or missed categories. Because we deal with an abundance of data across our platforms — such as IPS alerts, AMP alerts and more — feedback helps us
Beers with Talos EP 16: Strong Copy - Bad Rabbit and the Nyetya Connection
Beers with Talos (BWT) Podcast Episode 16 is now available. Download this episode and subscribe to Beers with Talos: The crew takes on Apache OpenOffice vulns and when you need one CVE versus one hundred. We spend a lot of time discussing signal to noise ratio and Twitter canar
Threat Spotlight: Upatre - Say No to Drones, Say Yes to Malware
Talos has observed an explosion of malicious downloaders in 2015 which we’ve documented on several occasions on our blog. These downloaders provide a method for attackers to push different types of malware to endpoint systems easily and effectively. Upatre is an example of a mali
Threat Spotlight: Angler Lurking in the Domain Shadows
Overview Over the last several months Talos researchers have been monitoring a massive exploit kit campaign that is utilizing hijacked registrant accounts to create large amounts of subdomains for both initial redirection and exploitation. This campaign has been largely attribu
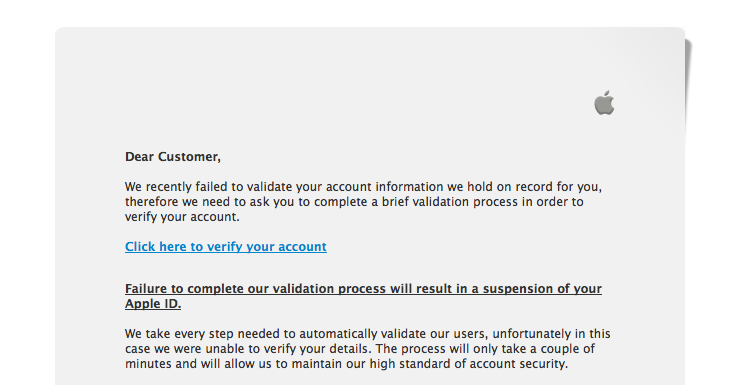
Apple ID Harvesting, now this is a good phish.
Phishing isn't new. "So, why are you writing about it?", you ask. I received this one today and it was very well done, so I thought I'd write it up. Chances are, you've seen these before: If you are familiar with Apple Verification emails, you'll not
Threat Spotlight: "A String of Paerls", Part 2, Deep Dive
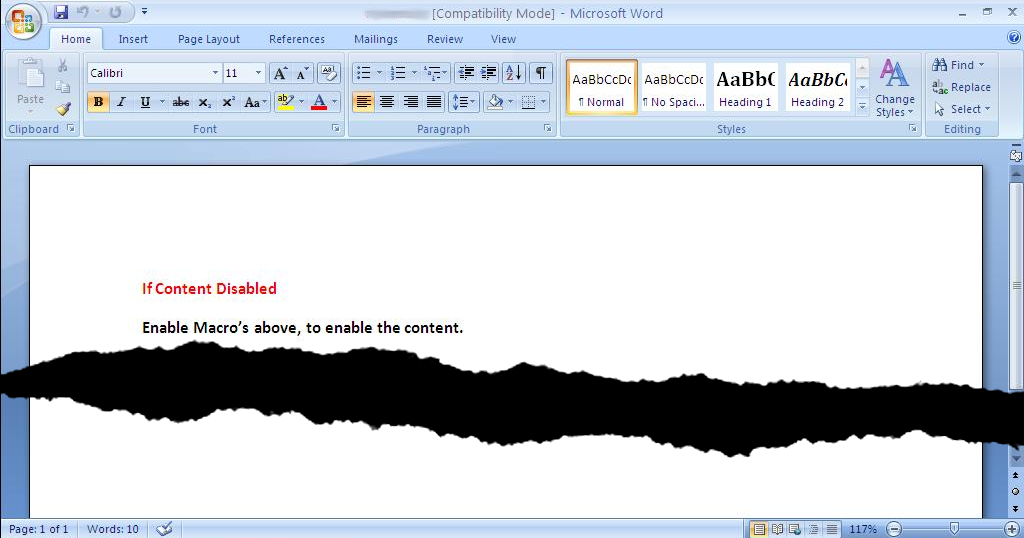
This post has been coauthored by Joel Esler, Craig Williams, Richard Harman, Jaeson Schultz, and Douglas Goddard In part one of our two part blog series on the “String of Paerls” threat, we showed an attack involving a spearphish message containing an attached malicious Word doc
Detection for PutterPanda, we got this.
Recently a post by Crowdstrike was released detailing an attack being used, allegedly, by the Chinese Military "PLA Unit 61486". The post is a great demonstration of the use of OSINT (Open Source Intelligence) to track an adversary in this increasingly digital world.
The never ending Exploit Kit shift - Bleeding Life
Recently we've been able to observe several shifts in exploit kit techniques, so I thought it would be good to share the IOC information for the exploit kits so that administrators and network defenders can take a look at their devices and logs to remediate on their networks.
Fiesta Exploit Kit, is no party
Recently, when our Cisco TRAC team contacted us about some work that we did concerning the Fiesta Exploit Kit for an article they were writing, we were happy to work with them. As discussed in the recent Cisco Annual Security Report, exploit kits have been very pervasive in the