Attribution: A Puzzle
By Martin Lee, Paul Rascagneres and Vitor Ventura. Introduction The attribution of cyber attacks is hard. It requires collecting diverse intelligence, analyzing it and deciding who is responsible. Rarely does the evidence available to researchers reach a level of proof that wo
Fingerprint cloning: Myth or reality?
Phone, computer fingerprint scanners can be defeated with 3-D printing By Paul Rascagneres and Vitor Ventura. Executive summary Passwords are the traditional authentication methods for computers and networks. But passwords can be stolen. Biometric authentication seems the pe
Bisonal: 10 years of play
By Warren Mercer, Paul Rascagneres and Vitor Ventura. Update 06/03/20: added samples from 2020. Executive summary * Security researchers detected and exposed the Bisonal malware over the past 10 years. But the Tonto team, the threat actor behind it, didn't stop. * Th
Sea Turtle keeps on swimming, finds new victims, DNS hijacking techniques
By Danny Adamitis with contributions from Paul Rascagneres. Executive summary After several months of activity, the actors behind the "Sea Turtle" DNS hijacking campaign are not slowing down. Cisco Talos recently discovered new details that suggest they regrouped af
DNSpionage brings out the Karkoff
Update 4/24: The C2 section below now includes details around the XOR element of the C2 communication system. Executive summary In November 2018, Cisco Talos discovered an attack campaign, called DNSpionage, in which threat actors created a new remote administrative tool that
GlitchPOS: New PoS malware for sale
Warren Mercer and Paul Rascagneres authored this post with contributions from Ben Baker. Executive summary Point-of-sale malware is popular among attackers, as it usually leads to them obtaining credit card numbers and immediately use that information for financial gain. This t
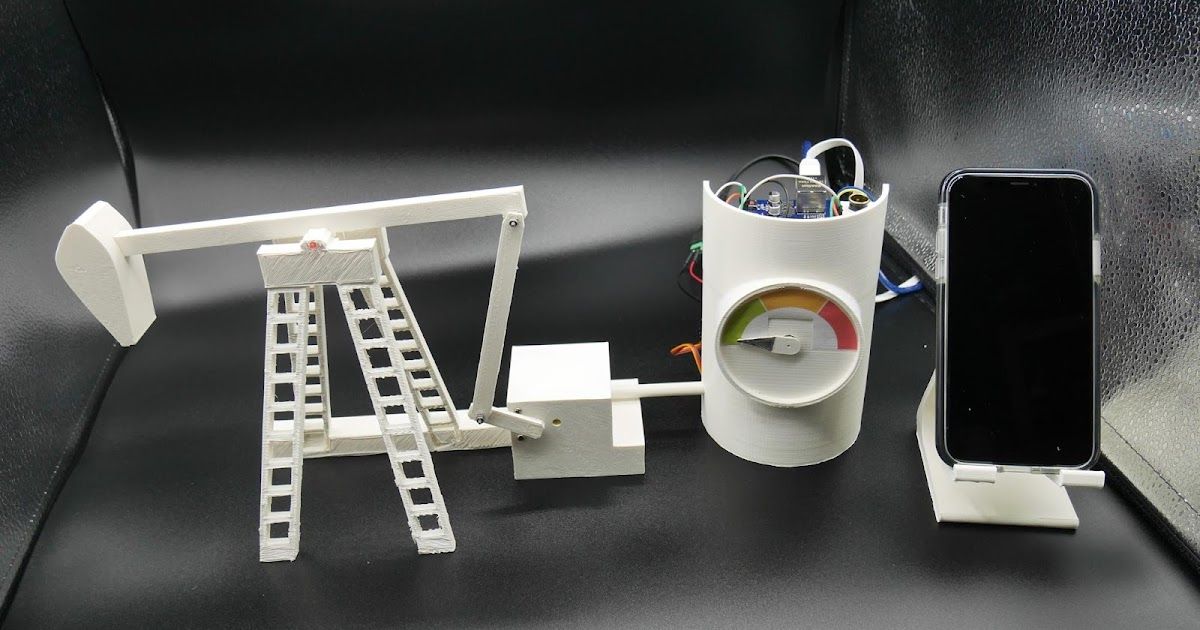
What you can learn from Cisco Talos’ new oil pumpjack workshop
There are a lot of ways in which researchers could utilize this system to research potential attack vectors on an oil pumpjack.
Fake Cisco Job Posting Targets Korean Candidates
Edmund Brumaghin and Paul Rascagneres authored this post, with contributions from Jungsoo An. Executive summary Cisco Talos recently observed a targeted malware campaign being leveraged in an attempt to compromise specific organizations. The infection vector associated with
Vulnerability Spotlight: Multiple WIBU SYSTEMS WubiKey vulnerabilities
Marcin "Icewall" Noga of Cisco Talos discovered these vulnerabilities. Executive Summary Cisco Talos discovered two vulnerabilities that could allow remote code execution and memory disclosure at the kernel level in WIBU-SYSTEMS WibuKey. WibuKey is a USB key designed