Rocke: The Champion of Monero Miners
This post was authored by David Liebenberg. Summary Cryptocurrency miners are becoming an increasingly significant part of the threat landscape. These malicious miners steal CPU cycles from compromised devices to mine cryptocurrencies and bring in income for the threat actor.
Blocking Cryptocurrency Mining Using Cisco Security Products
Cisco Talos is releasing a whitepaper addressing Cryptocurrency mining and all the ways to block it using Cisco Security products. The value of cryptocurrencies has fluctuated wildly, but the value is still high enough to garner a lot of attention, both legitimate and malicious.
Cryptomining Campaign Returns Coal and Not Diamond
Ransom Where? Malicious Cryptocurrency Miners Takeover, Generating Millions
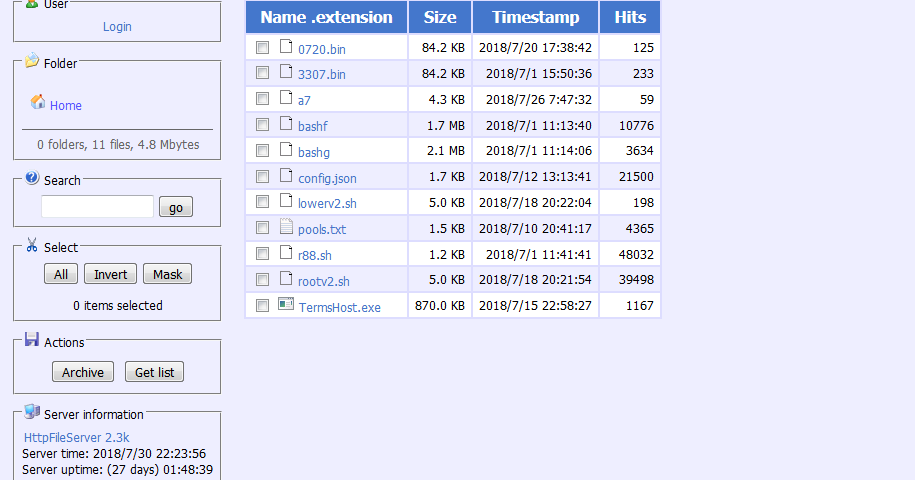
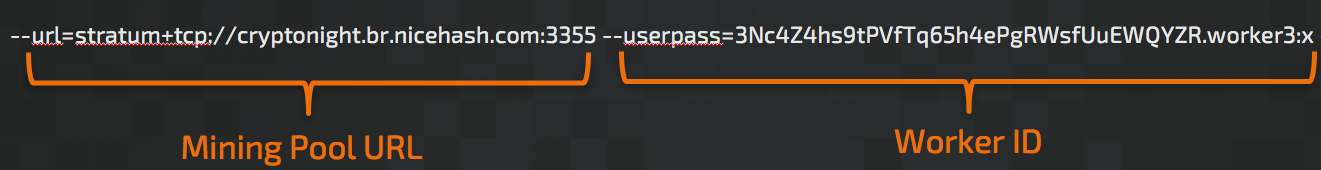
his post was authored by Nick Biasini, Edmund Brumaghin, Warren Mercer and Josh Reynolds with contributions from Azim Khodijbaev and David Liebenberg. Executive Summary The threat landscape is constantly changing; over the last few years malware threat vectors, methods and pay