Pumpkin Spiced Locky
This post was authored by Warren Mercer & Edmund Brumaghin Summary We had .locky, we had .odin and then we had .zepto but today we hit rock bottom and we now have Locky using .shit as their encrypted file extension. In today's latest wave of spam, Talos has observed
MBRFilter - Can't Touch This!
Update: 10/20/2016 - MBRFilter has been intentionally made difficult to remove to prevent malware from simply disabling or removing this protection during the infection process. Test thoroughly before deploying within production environments. Summary Ransomware has become incr
LockyDump - All Your Configs Are Belong To Us
This post was authored by Warren Mercer and Matthew Molyett Summary Locky has continued to evolve since its inception in February 2016. This has made it difficult to track at times due to changes in the way in which it's distributed as well as various characteristics of the
Ransomware: Because OpSec is Hard?
This blog was authored by Edmund Brumaghin and Warren Mercer Summary Talos recently published research regarding a new variant of destructive ransomware, which we dubbed Ranscam. During further analysis of Ranscam samples, we discovered several indicators of compromise (IOCs
When Paying Out Doesn't Pay Off
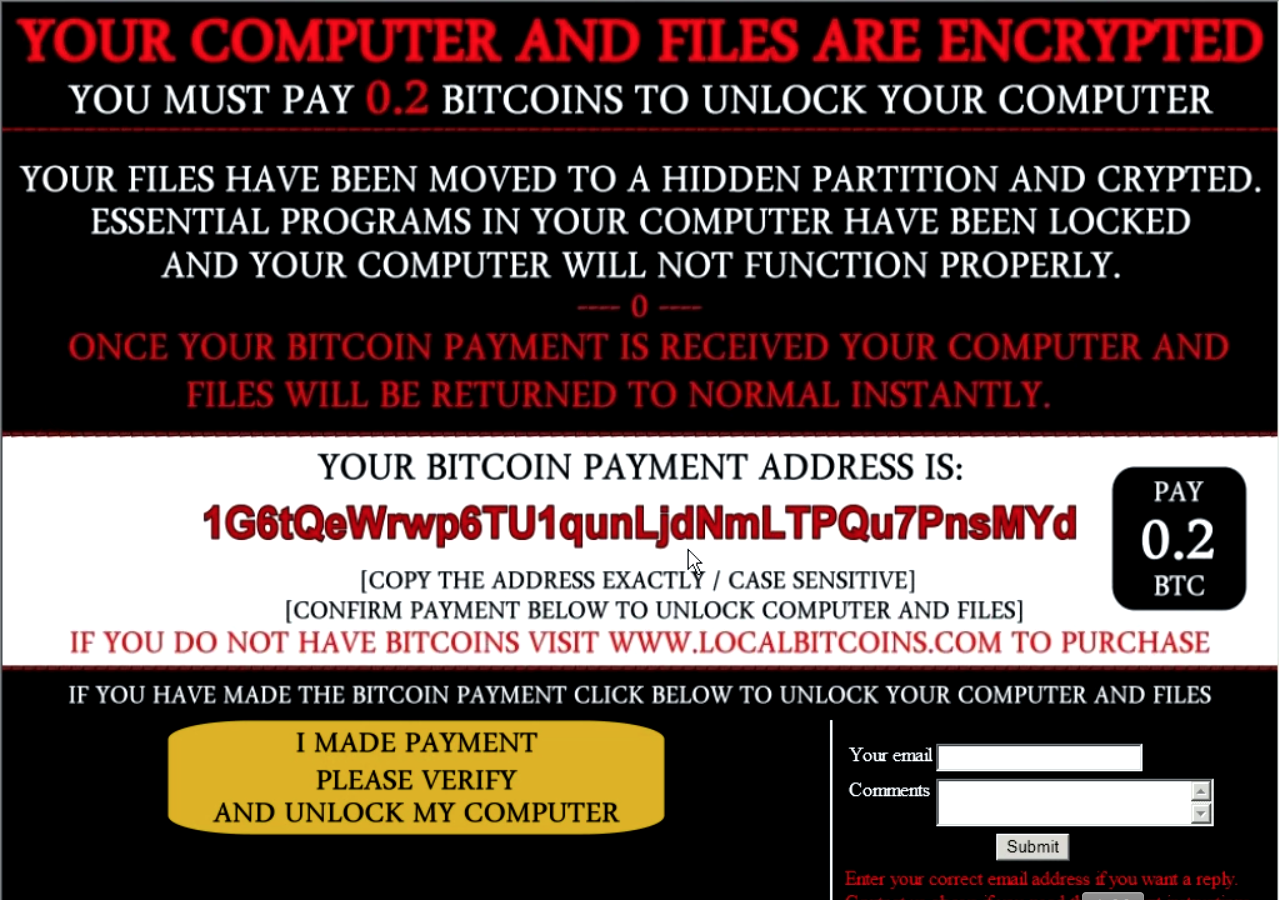
This blog post was authored by Edmund Brumaghin and Warren Mercer Summary Talos recently observed a new ransomware variant targeting users. This ransomware shows that new threat actors are continuing to enter the ransomware market at a rapid pace due to the lucrative nature of
Connecting the Dots Reveals Crimeware Shake-up
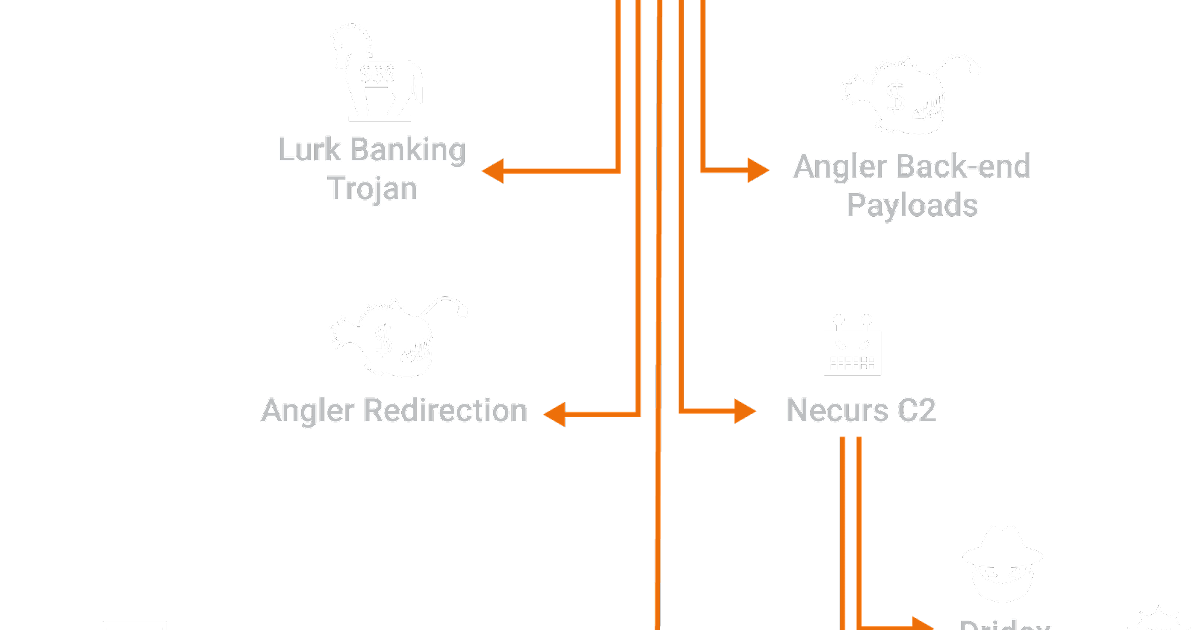
This Post Authored by Nick Biasini For a couple of weeks in June the threat landscape was changed. Several high profile threats fell off the scene, causing a shake-up that hadn't been seen before. For a period of three weeks the internet was safer, if only for a short time.
Gotta be SWIFT for this Spam Campaign!
This blog post was authored by Warren Mercer Summary Talos have observed a large uptick in the Zepto ransomware and have identified a method of distribution for the Zepto ransomware, Spam Email. Locky/Zepto continue to be well known ransomware variants and as such we will focus
Cryptolocker 4 White Paper Available: The Evolution Continues
We are pleased to announce the availability of the Cryptolocker 4 white paper. Over the past year, Talos has devoted a significant amount of time to better understanding how ransomware operates, its relation to other malware, and its economic impact. This research has proven valu
Widespread JBoss Backdoors a Major Threat
Recently a large scale ransomware campaign delivering Samsam changed the threat landscape for ransomware delivery. Targeting vulnerabilities in servers to spread ransomware is a new dimension to an already prolific threat. Due to information provided from our Cisco IR Services Te