Threat Roundup Sept 28 - Oct 5
Today, as we do every week, Talos is giving you a glimpse into the most prevalent threats we’ve observed this week — covering the dates between Sept. 28 and Oct. 5. As with previous roundups, this post isn’t meant to be an in-depth analysis. Instead, we will summarize the threats
Threat Roundup Sept 21 - 28
Today, as we do every week, Talos is giving you a glimpse into the most prevalent threats we’ve observed this week — covering the dates between Sept. 21 and 28. As with previous roundups, this post isn’t meant to be an in-depth analysis. Instead, we will summarize the threats we
TeleGrab - Grizzly Attacks on Secure Messaging
The malware is mainly targeting Russian-speaking victims, and is intentionally avoiding IP addresses related with anonymizer services.
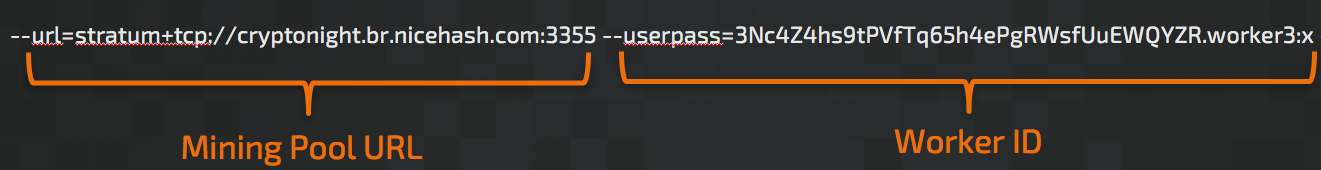
Ransom Where? Malicious Cryptocurrency Miners Takeover, Generating Millions
his post was authored by Nick Biasini, Edmund Brumaghin, Warren Mercer and Josh Reynolds with contributions from Azim Khodijbaev and David Liebenberg. Executive Summary The threat landscape is constantly changing; over the last few years malware threat vectors, methods and pay
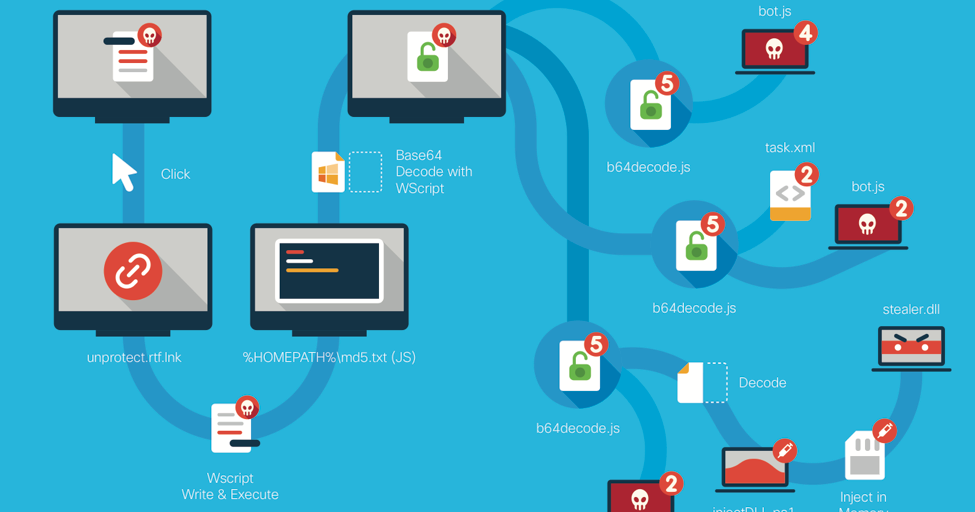
FIN7 Group Uses JavaScript and Stealer DLL Variant in New Attacks
This post was authored by Michael Gorelik and Josh Reynolds Executive Summary Throughout this blog post we will be detailing a newly discovered RTF document family that is being leveraged by the FIN7 group (also known as the Carbanak gang) which is a financially-motivated grou
Threat Round-up for July 14 - July 21
Today, Talos is publishing a glimpse into the most prevalent threats we've observed between July 14 and July 21. As with previous round-ups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting
Threat Round-up for May 19 - May 26
Today, Talos is publishing a glimpse into the most prevalent threats we've observed between May 19 and May 26. As with previous round-ups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting ke
Reversing Multilayer .NET Malware
This post was authored by Dave McDaniel with contributions from Jaeson Schultz. Recently, we came across a malware sample that has been traversing the Internet disguised as an image of a woman. The malware sample uses several layers of obfuscation to hide its payload, including
Threat Spotlight: Group 72, Opening the ZxShell
This post was authored by Andrea Allievi, Douglas Goddard, Shaun Hurley, and Alain Zidouemba. Recently, there was a blog post on the takedown of a botnet used by threat actor group known as Group 72 and their involvement in Operation SMN. This group is sophisticated, well funde