Ransomware and pre-ransomware engagements make up 40 percent of threats seen this quarter
For the first time since compiling these reports, Cisco Talos Incident Response saw an equal number of ransomware and pre-ransomware engagements, making up nearly 40 percent of threats this quarter.
It can be difficult to determine what constitutes a pre-ransomware attack if ransomware never executes and encryption does not take place. However, Talos IR assesses that the combination of Cobalt Strike and credential-harvesting tools like Mimikatz, paired with enumeration and discovery techniques, indicates a high likelihood that ransomware is the final objective.
This quarter featured a variety of publicly available tools and scripts hosted on GitHub repositories or other third-party websites to support operations across multiple stages of the attack lifecycle. This activity coincides with a general increase in the use of other dual-use tools, such as the legitimate red-teaming tool Brute Ratel and the recently discovered Manjusaka and Alchimist attack frameworks.

Targeting
Attackers targeted the education sector the most of any vertical this quarter, closely followed by the financial services, government, and energy sectors, respectively. For the first time since Q4 2021, telecommunications was not the top-targeted vertical. While the reason for the education sector being more frequently targeted this quarter is unknown, this is a popular time of year for adversaries to target education institutions as students and teachers return to school.

Ransomware
We observed two previously seen high-profile ransomware families, Vice Society and Hive. This quarter also saw a ransomware family that had yet to be observed in IR engagements, Black Basta, which first emerged in April 2022.
Talos IR responded to a Vice Society ransomware engagement affecting an education institution in Austria, part of an ongoing trend of Vice Society actors disproportionately targeting the education sector, which is consistent with U.S. Cybersecurity and Infrastructure Security Agency (CISA) reporting. Analysis of the event logs revealed numerous outbound remote desktop protocol (RDP) connection attempts from an infected host to other systems, indicating the adversary moved laterally. Further analysis identified indicators for remote access software AnyDesk and TeamViewer, where over 50 systems were observed reaching out to TeamViewer-related URLs. An exception was also added to the Windows Defender firewall exemption list for “AnyDesk.exe” executions by the SYSTEM account. The likely trigger for ransomware was PsExec execution followed by deployment of ransomware, which was written to the Windows Roaming profile of the compromised user.
In recent months, Talos observed ongoing Qakbot activity leveraging thread hijacking and password-protected ZIP files to enhance legitimacy. For example, in a ransomware engagement affecting a U.S.-based IT company, Talos IR observed multiple IP addresses associated with command and control (C2) traffic to/from compromised endpoints associated with Qakbot. The attackers likely gained initial access via a phishing email with an HTML attachment that, once opened, initiated JavaScript that subsequently downloaded a malicious password-protected ZIP file. The ZIP file contained a Windows shortcut file (LNK) that, once downloaded and executed on the victim system, delivers Qakbot. The adversaries eventually dropped the ransomware Black Basta, which we had not previously observed in Talos IR engagements. In the past six months, we’ve seen Qakbot use several different infection chains, including potentially moving away from LNK files in some campaigns.
Talos has been monitoring the disclosure of “LockBit Black,” the builder for the LockBit 3.0 ransomware encryptor, leaked publicly in late September 2022 by an alleged LockBit coder/developer. This leak is among many setbacks this group has experienced in recent months, including distributed denial-of-service (DDoS) attacks targeting the group’s data leaks site. While Talos IR did not observe any LockBit ransomware engagements this quarter, the builder could make attribution more difficult involving typical LockBit tactics, techniques, and procedures (TTPs) as more threat actors incorporate the builder in their own ransomware operations. Talos has already begun tracking one new ransomware group dubbed “BlooDy Gang” which has reportedly used the leaked LockBit 3.0 builder in recent ransomware attacks. This could enable even more ransomware groups to save time and resources by relying on leaked builders and source code of other ransomware operations, as opposed to independently developing ransomware.
Uptick in pre-ransomware behaviors
While ransomware was the top threat this quarter, we also observed an equal number of engagements involving various pre-ransomware behaviors. Although each pre-ransomware engagement involves unique behaviors and TTPs, the overwhelming similarities among these engagements include host enumeration, multiple credential-harvesting activities, and attempts to escalate privileges via an identified weakness or vulnerability in order to move laterally to other systems. In some instances where ransomware was never deployed, the adversary was likely trying to exfiltrate data at the time of detection, indicating they had broad enough access to cause significant harm at that time.
In a pre-ransomware engagement affecting a European energy company, Talos IR observed the installation of Cobalt Strike and Mimikatz. The customer first observed Cobalt Strike installation and/or Mimikatz invocation affecting nearly 100 servers. Talos IR detected traffic associated with Metasploit Framework’s Meterpreter shell originating from a compromised host. Seven minutes later, the system attempted to reach out to a confirmed Cobalt Strike C2 server. PowerShell commands and scripts revealed a lightweight Cobalt Strike loader likely associated with Cobalt Strike SMB lateral beaconing. Other tools observed in the environment include the Active Directory mapping tool SharpHound and Rubeus, a Kerberoasting tool.
Multiple publicly available tooling and scripts support adversary objectives
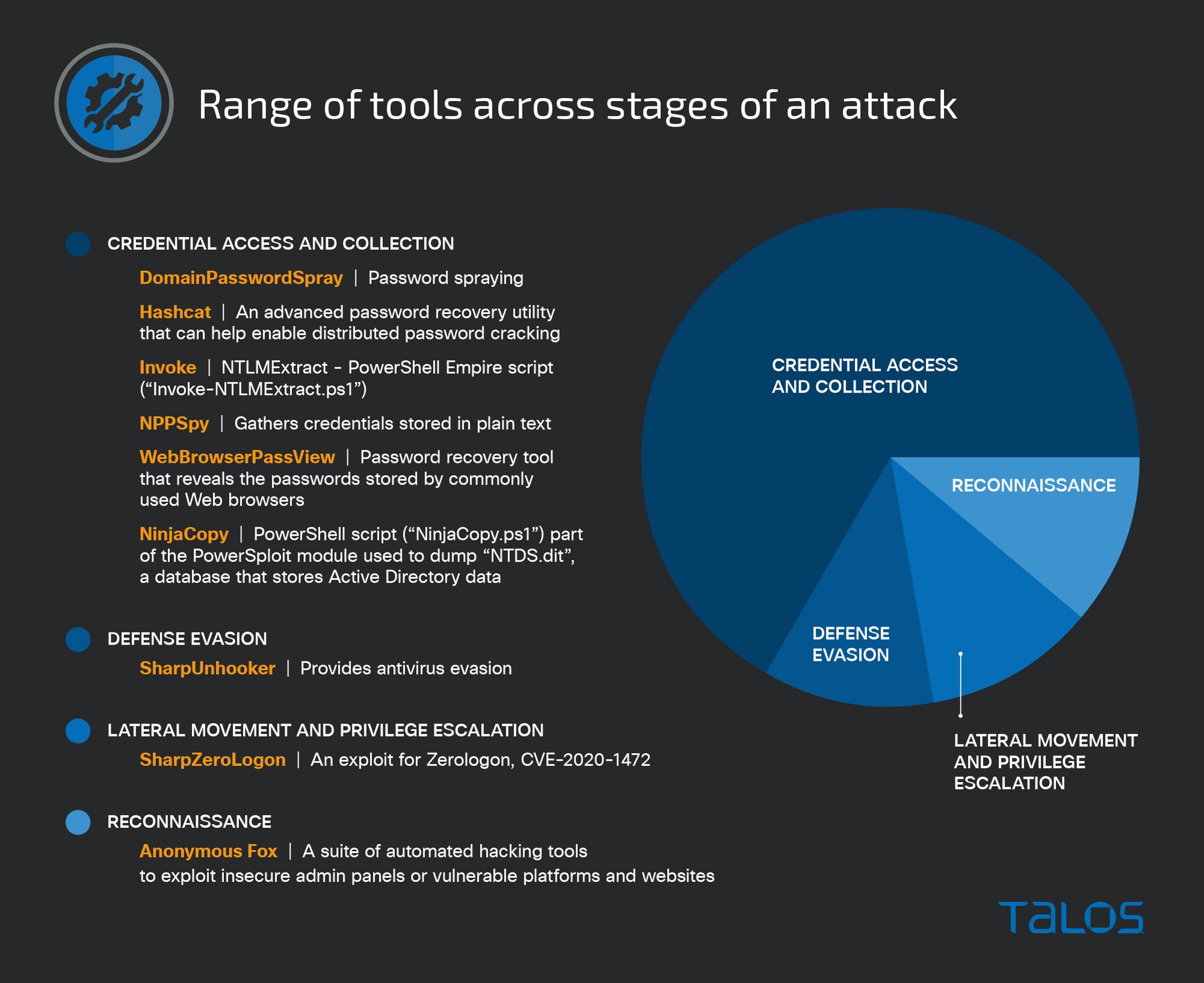
We observed adversaries leveraging a variety of publicly available tools and scripts hosted on GitHub repositories or free to download from third-party websites to support operations across multiple stages of the attack lifecycle. To support an adversary's objectives, we commonly observed offensive security and red-team tools, such as the modularized Cobalt Strike framework and Active Directory reconnaissance tools ADFind and BloodHound. However, the presence of these additional scripts and tools indicates that adversaries are continuing to identify publicly available resources, which adds convenience but muddies attribution.
In a pre-ransomware incident affecting a U.S. manufacturer, the adversary logged in and executed a publicly available PowerShell script (“DomainPasswordSpray.ps1”) to perform password spraying against the domain. A technique to obtain credentials, password spraying is performed by using a single password, or a list of commonly used passwords, against many different accounts to attempt to validate credentials and gain access. The PowerShell script will result in large numbers of account lockouts, which match the activity reported by the customer. Talos IR also identified the presence of SharpZeroLogon, an exploit for the Zerologon (CVE-2020-1472) privilege escalation vulnerability, which is publicly available on GitHub. Ultimately, this allows an attacker to take control of a domain controller by resetting the account of the targeted domain controller, potentially leading to a full domain admin compromise.
Talos has been monitoring the increased use of dual-use tools such as Cobalt Strike, Brute Ratel, Sliver, and Manjusaka. Brute Ratel is of particular concern since the toolkit was cracked in late September and is being shared for free across several hacking forums and communities. Additionally, endpoint telemetry revealed an attack chain with Qakbot dropping Brute Ratel. Although we have not yet observed Brute Ratel in any Talos IR engagements, we assess that the tool’s rise in the cyber threat landscape in recent months, coinciding with Qakbot operators’ use and the cracked version, will likely lead to more threat actors adopting the post-exploitation kit into their operations.
Of note, a majority of the publicly available tooling leveraged this quarter appears focused on accessing and collecting credentials, highlighting the role these tools play in potentially furthering an adversary’s objectives.
Initial vectors
This quarter featured several engagements where attackers leveraged valid accounts to gain initial access, especially in cases where accounts were misconfigured, not disabled properly, or had weak passwords. In at least two engagements this quarter, Talos IR investigated the possibility of initial adversary access via a compromised contractor’s network or a contractor’s personal computer.
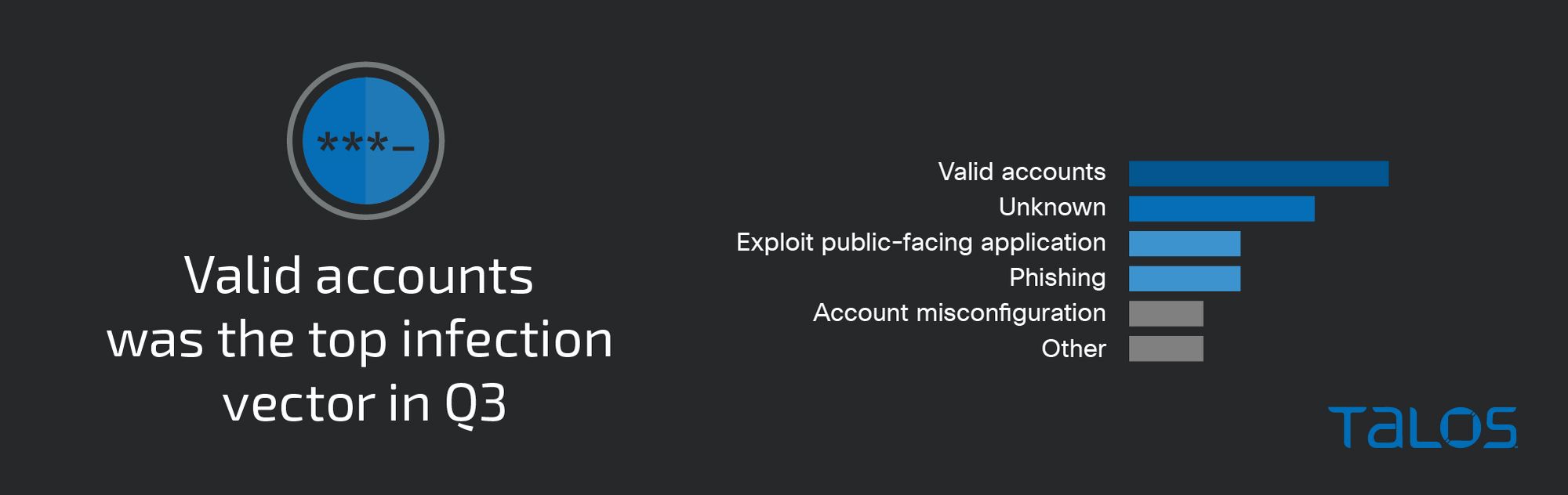
In nearly 15 percent of engagements this quarter, adversaries identified and/or exploited misconfigured public-facing applications by conducting SQL injection attacks against external websites, exploiting Log4Shell in vulnerable versions of VMware Horizon, and targeting misconfigured and/or publicly exposed servers.
We continued to see successful Log4Shell (CVE-2021-44228, CVE-2021-45046, and related flaws) exploitation attempts followed by a variety of malicious activities, such as cryptocurrency mining and ransomware. In a Hive ransomware incident affecting a U.S. education institution, Talos IR observed multiple Log4Shell exploitation attempts against a vulnerable VMware Horizon server, the most notable of these attempts resulted in a Cobalt Strike beacon dropped on the server. Talos IR also identified high volumes of cryptocurrency miners, which are common post-exploitation payloads associated with activity targeting the Log4j vulnerabilities. While we could not link the Hive affiliate to the Log4j exploitation attempts, VMware and its respective logs revealed that the server was public-facing, suggesting that more than one adversary may have attempted to target this vulnerability.
The next most common initial infection vector came via email followed by user execution of a malicious document or link. In one of the business email compromise (BEC) engagements affecting a U.S. financial services organization, the adversaries used thread-hijacking and a malicious email link which appeared to be a fake authentication page that collected user credentials upon entering. The adversary also enabled email inbox rules in an attempt to gain persistence on the compromised email account.
It is important to note that for the majority of incidents, Talos IR could not reasonably determine the initial vector because of logging deficiencies or a lack of visibility into the affected environment.
Security weaknesses
A lack of MFA remains one of the biggest impediments to enterprise security. Nearly 18 percent of engagements either had no MFA or only had it enabled on a handful of accounts and critical services. Talos IR frequently observes ransomware and phishing incidents that could have been prevented if MFA had been properly enabled on critical services, such as endpoint detection and response (EDR) solutions. Talos IR recommends disabling VPN access for all accounts that are not using two-factor authentication.
In what appears to be a prevalent theme this quarter, in 27 percent of engagements password or account access was not properly configured/disabled, leaving these accounts functionally active and allowing adversaries to use valid credentials to enter the environment. In a few cases, organizations did not properly disable account access after an employee left the organization. Talos IR’s recommendation is to disable or delete inactive accounts from Active Directory to prevent suspicious activity.
Top-observed MITRE ATT&CK techniques
Below is a list of the MITRE ATT&CK techniques observed in this quarter’s IR engagements. Given that some techniques can fall under multiple tactics, we grouped them under the most relevant tactic in which they were leveraged. The table below represents the techniques used with a relevant example, and the approximate number of times seen. However, it is not an exhaustive list.
Key findings from the MITRE ATT&CK appendix include:
- Legitimate remote access software, such as AnyDesk and TeamViewer, was leveraged in nearly a quarter of engagements.
- In an ongoing trend, adversaries leveraged valid accounts for initial access, especially notable where accounts were misconfigured or had weak passwords.
- We observed adversaries transferring tools or scripts from external systems or adversary-controlled infrastructure into a compromised environment, referred to as ingress tool transfer. The adversaries frequently downloaded these tools from public sites such as GitHub.
- We observed adversaries deploying Cobalt Strike and Mimikatz across several pre-ransomware engagements. In cases where ransomware encryption took place, PsExec usage played a large role in executing ransomware in 75 percent of ransomware engagements this quarter.
Tactic | Technique | Example |
|---|---|---|
Initial Access (TA0001) | T1078 Valid Accounts | Adversary leveraged stolen or compromised credentials |
Reconnaissance (TA0043) | T1592 Gather Victim Host Information | Text file contains details about host |
Persistence (TA0003) | T1136 Create Account | Created a user to add to the local administrator’s group |
Execution (TA0002) | T1059.001 Command and Scripting Interpreter: PowerShell | Executes PowerShell code to retrieve information about the client's Active Directory environment |
Discovery (TA0007) | T1482 Domain Trust Discovery | Use various utilities to identify information on domain trusts |
Credential Access (TA0006) | T1003 OS Credential Dumping | Deploy Mimikatz and publicly available password lookup utilities |
Privilege Escalation (TA0004) | T1068 Exploitation for Privilege Escalation | Exploit ZeroLogon to escalate privileges with a direct path to a compromised domain |
Lateral Movement (TA0008) | T1021.001 Remote Desktop Protocol | Adversary made attempts to move laterally using Windows Remote Desktop |
Defense Evasion (TA0005) | T1027 Obfuscated Files or Information | Use base64-encoded PowerShell scripts |
Command and Control (TA0011) | T1105 Ingress Tool Transfer | Adversaries transfer/download tools from an external system |
Impact (TA0040) | T1486 Data Encrypted for Impact | Deploy Hive ransomware and encrypt critical systems |
Exfiltration (TA0010) | T1567.002 Exfiltration Over Web Service: Exfiltration to Cloud Storage | Actor exfiltrated data to file sharing site mega[.]nz |
Collection (TA0009) | T1074 Data Staged | Stage data in separate output files |
Software/Tool | S0002 Mimikatz | Use Mimikatz to obtain account logins and passwords |