Let's Destroy Democracy
* /what-to-expect-when-youre-electing * /election-roundtable-video * /what-to-expect-electing-disinformation-building-blocks Executive summary Over the past few years, Cisco Talos has increasingly been involved in election security research and support, most recently support
Welcome Spelevo: New exploit kit full of old tricks
EXECUTIVE SUMMARY Exploit kits are an ever-present and often forgotten threat on the landscape today. Their popularity seemed to peak several years ago with the success and eventual downfall of some of the best compromise platforms ever created, including the Angler Exploit Kit.
Using Firepower to defend against encrypted RDP attacks like BlueKeep
This blog was authored by Brandon Stultz Microsoft recently released fixes for a critical pre-authentication remote code execution vulnerability in Remote Desktop Protocol Services (RDP). Identified as CVE-2019-0708 in May's Patch Tuesday, the vulnerability caught the attent
Threat Roundup for May 17 to May 24
Today, Talos is publishing a glimpse into the most prevalent threats we've observed between May 17 and May 24. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting ke
Threat Roundup for April 26 to May 3
Today, Talos is publishing a glimpse into the most prevalent threats we've observed between April 26 and May 03. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting k
Sextortion profits decline despite higher volume, new techniques
Sextortion spammers continue blasting away at high volume. The success they experienced with several high-profile campaigns last year has led these attackers to continue transmitting massive amounts of sextortion email. These sextortion spammers have been doing everything they ca
Ransomware or Wiper? LockerGoga Straddles the Line
Executive Summary Ransomware attacks have been in the news with increased frequency over the past few years. This type of malware can be extremely disruptive and even cause operational impacts in critical systems that may be infected. LockerGoga is yet another example of this sor
Connecting the dots between recently active cryptominers
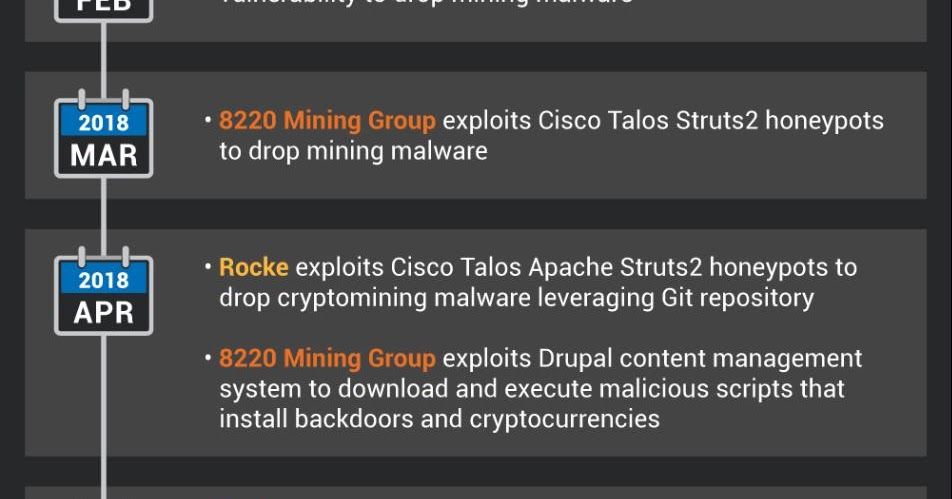
Post authored by David Liebenberg and Andrew Williams. Executive Summary Through Cisco Talos' investigation of illicit cryptocurrency mining campaigns in the past year, we began to notice that many of these campaigns shared remarkably similar TTPs, which we at first mistak