The sights and sounds from the Talos Threat Research Summit
Cyber Security Week in Review (March 28)
Ransomware or Wiper? LockerGoga Straddles the Line
Executive Summary Ransomware attacks have been in the news with increased frequency over the past few years. This type of malware can be extremely disruptive and even cause operational impacts in critical systems that may be infected. LockerGoga is yet another example of this sor
Files Cannot Be Decrypted? Challenge Accepted. Talos Releases ThanatosDecryptor
This blog post was authored by Edmund Brumaghin, Earl Carter and Andrew Williams. Executive summary Cisco Talos has analyzed Thanatos, a ransomware variant that is being distributed via multiple malware campaigns that have been conducted over the past few months. As a result of
Gandcrab Ransomware Walks its Way onto Compromised Sites
This blog post authored by Nick Biasini with contributions from Nick Lister and Christopher Marczewski. Despite the recent decline in the prevalence of ransomware in the threat landscape, Cisco Talos has been monitoring the now widely distributed ransomware called Gandcrab. Gand
Ransom Where? Malicious Cryptocurrency Miners Takeover, Generating Millions
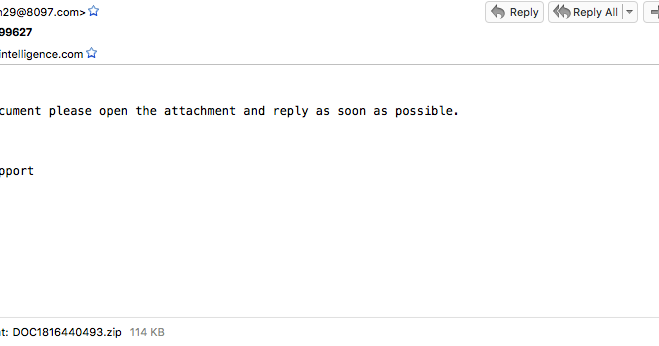
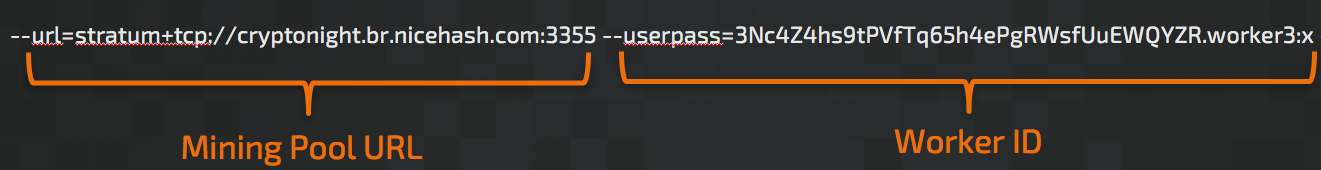
his post was authored by Nick Biasini, Edmund Brumaghin, Warren Mercer and Josh Reynolds with contributions from Azim Khodijbaev and David Liebenberg. Executive Summary The threat landscape is constantly changing; over the last few years malware threat vectors, methods and pay
SamSam - The Evolution Continues Netting Over $325,000 in 4 Weeks
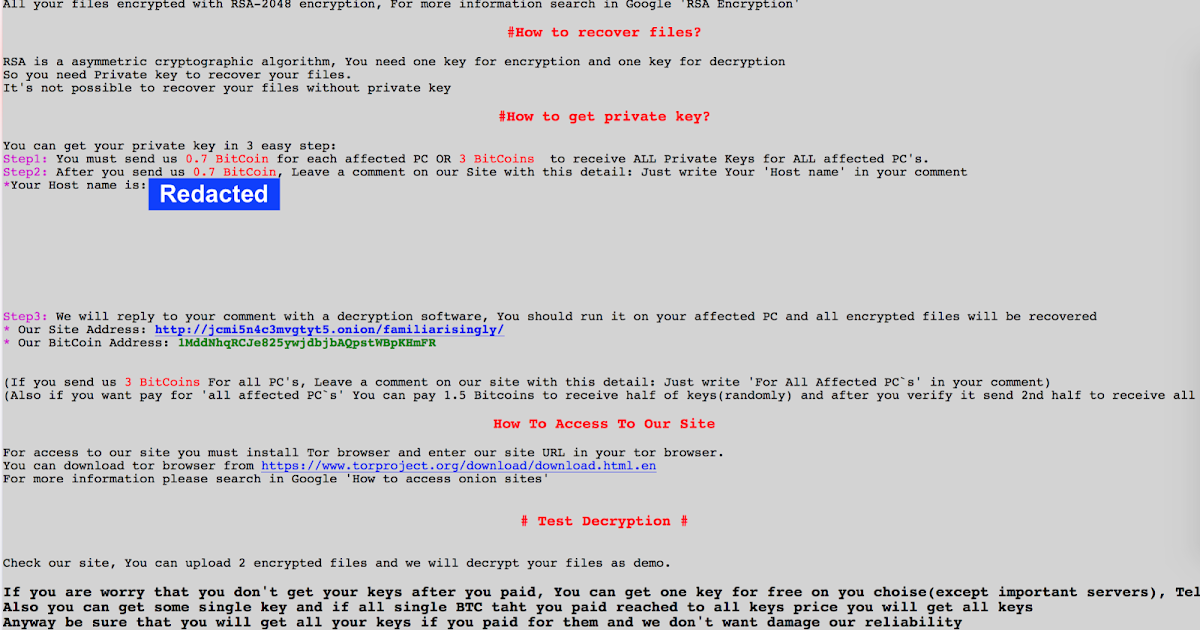
This post was written by Vitor Ventura Introduction Talos has been working in conjunction with Cisco IR Services on what we believe to be a new variant of the SamSam ransomware. This ransomware has been observed across multiple industries including Government, Healthcare and
Threat Spotlight: Follow the Bad Rabbit
Note: This blog post discusses active research by Talos into a new threat. This information should be considered preliminary and will be updated as research continues. Update 2017-10-26 16:10 EDT: added additional information regarding the links between Nyetya and BadRabbit Upd
Back to Basics: Worm Defense in the Ransomware Age
This post was authored by Edmund Brumaghin "Those who cannot remember the past are condemned to repeat it." - George Santayana The Prequel In March 2017, Microsoft released a security update for various versions of Windows, which addressed a remote code execution vu