What to expect when you're electing: The building blocks of disinformation campaigns
By Nick Biasini, Kendall McKay and Matt Valites. Editor's note: Related reading on Talos election security research: * /what-to-expect-when-youre-electing * /election-roundtable-video * /what-to-expect-electing-disinformation-building-blocks As Cisco Talos discovered du
Adversarial use of current events as lures
The goal of malicious activity is to compromise the system to install some unauthorized software. Increasingly that goal is tied to one thing: the user. Over the past several years, we as an industry improved exploit mitigation and the value of working exploits has increased acco
Vulnerability Spotlight: Zoom Communications user enumeration
Video conferencing and calling software has spiked in popularity as individuals across the globe are forced to stay home due to the COVID-19 pandemic. There are a plethora of players in this space, with one or two getting increased attention. One service in particular — Zoom — ha
Threat actors attempt to capitalize on coronavirus outbreak
* Coronavirus is dominating the news and threat actors are taking advantage. * Cisco Talos has found multiple malware families being distributed with Coronavirus lures and themes. This includes emotet and several RAT variants. Executive Summary Using the news to try and incr
What the continued escalation of tensions in the Middle East means for security
Cisco Talos works with many organizations around the world, monitoring and protecting against sophisticated threats every day. As such, we are watching the current state of events in the Middle East very closely for our customers and partners who may be impacted by the ongoing si
Incident Response lessons from recent Maze ransomware attacks
By JJ Cummings and Dave Liebenberg This year, we have been flooded with reports of targeted ransomware attacks. Whether it's a city, hospital, large- or medium-sized enterprise — they are all being targeted. These attacks can result in significant damage, cost, and have many
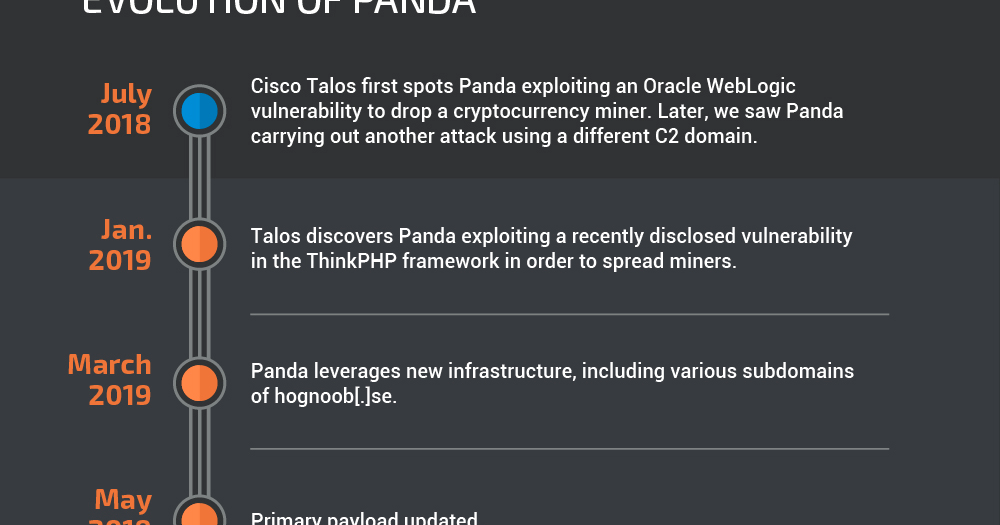
Cryptocurrency miners aren’t dead yet: Documenting the voracious but simple “Panda”
By Christopher Evans and David Liebenberg. Executive summary A new threat actor named "Panda" has generated thousands of dollars worth of the Monero cryptocurrency through the use of remote access tools (RATs) and illicit cryptocurrency-mining malware. This is far fr
Threat Roundup for July 26 to Aug. 2
Today, Talos is publishing a glimpse into the most prevalent threats we've observed between July 26 and Aug. 2. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting ke
Malvertising: Online advertising's darker side
Executive summary One of the trickiest challenges enterprises face is managing the balance between aggressively blocking malicious advertisements (aka malvertising) and allowing content to remain online, accessible for the average user. The days of installing a basic ad blocker