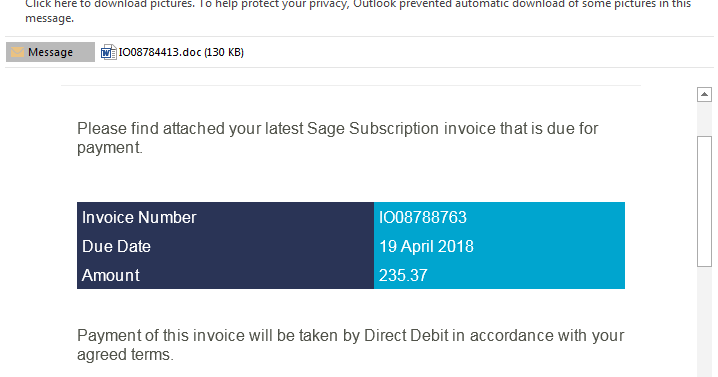
Smoking Guns - Smoke Loader learned new tricks
Smoke Loader is primarily used as a downloader to drop and execute additional malware like ransomware or cryptocurrency miners.
Threat Spotlight: Mighty Morphin Malware Purveyors: Locky Returns Via Necurs
Throughout the majority of 2016, Locky was the dominant ransomware in the threat landscape. It was an early pioneer when it came to using scripting formats Windows hosts would natively handle, like .js, .wsf, and .hta. These scripting formats acted as a vehicle to deliver the pay
Take the RIG Pill: Down the Rabbit Hole
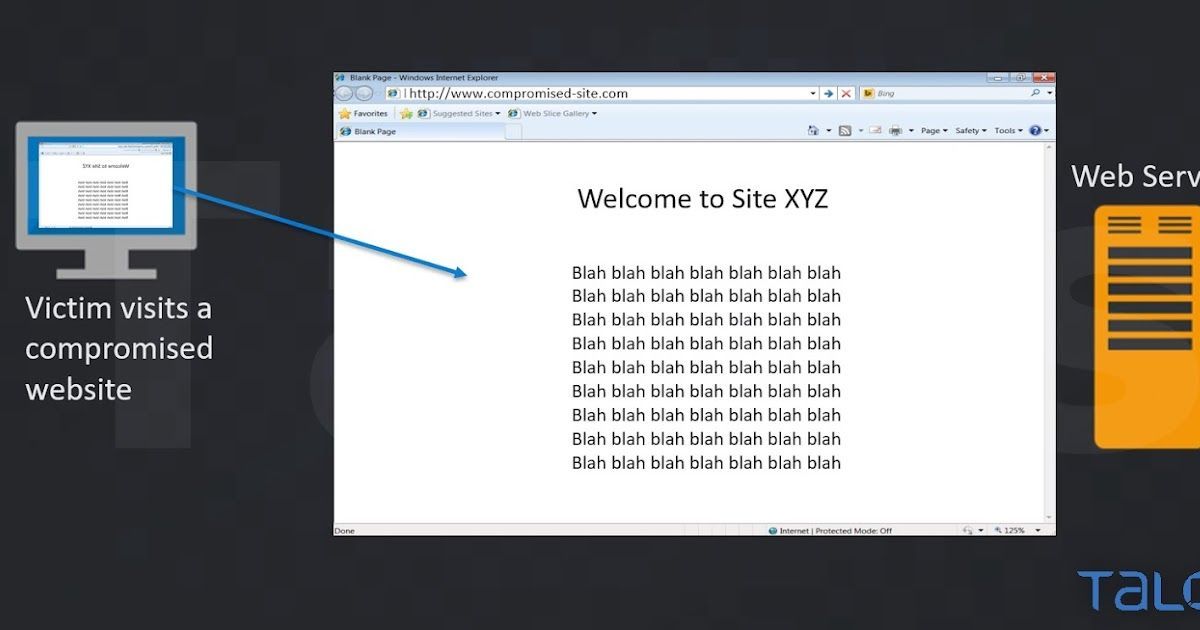
The adversaries are leveraging Gates (e.g. EITest) to redirect the users to their Landing Page. This leads to a chain of redirects, before the victim finally gets on the landing page of the exploit kit.
Threat Spotlight: Spin to Win...Malware
This post was authored by Nick Biasini with contributions from Tom Schoellhammer and Emmanuel Tacheau. The threat landscape is ever changing and adversaries are always working to find more efficient ways to compromise users. One of the many ways that users are driven to maliciou
Threat Spotlight: Exploit Kit Goes International Hits 150+ Countries
Overview Talos is constantly monitoring the threat landscape and exploit kits are a constantly evolving component of it. An ongoing goal of Talos is to expose and disrupt these kits to protect the average internet user being targeted and compromised. We were able to gain unprece
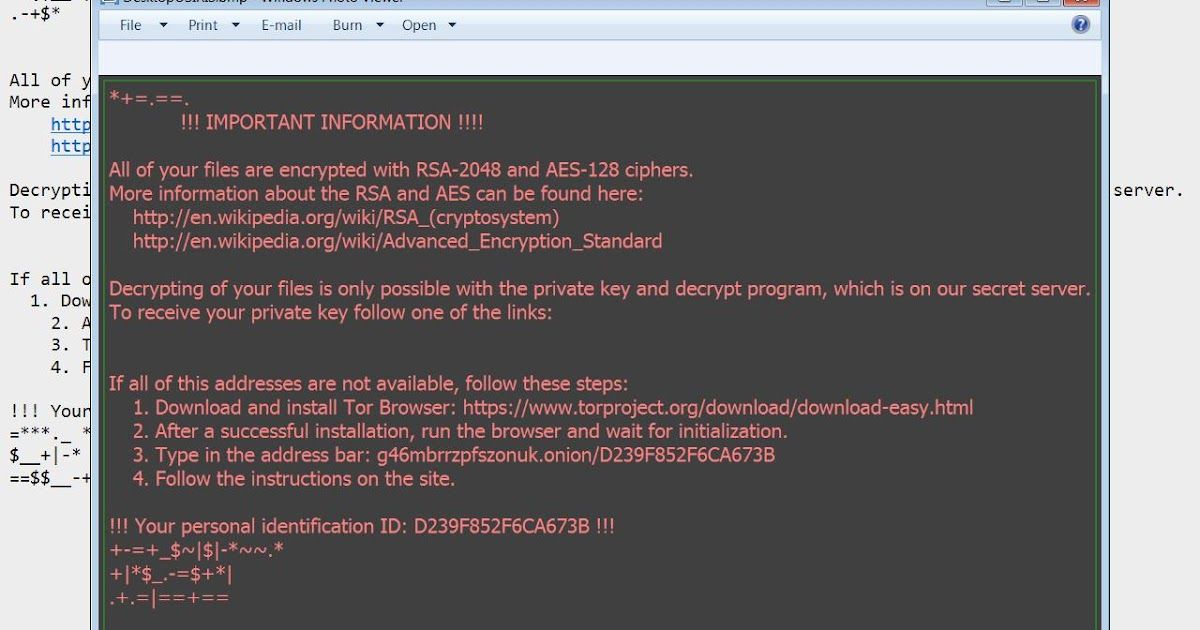
Ransomware: Past, Present, and Future
"What's past is prologue." -- William Shakespeare, The Tempest Introduction The rise of ransomware over the past year is an ever growing problem. Businesses often believe that paying the ransom is the most cost effective way of getting their data back - and this
Threat Spotlight: Rombertik - Gazing Past the Smoke, Mirrors, and Trap Doors
This post was authored by Ben Baker and Alex Chiu. Executive Summary Threat actors and security researchers are constantly looking for ways to better detect and evade each other. As researchers have become more adept and efficient at malware analysis, malware authors have mad
Threat Spotlight: TeslaCrypt - Decrypt It Yourself
This post was authored by: Andrea Allievi, Earl Carter & Emmanuel Tacheau Update 4/28: Windows files recompiled with backward compatibility in Visual Studio 2008 Update 5/8: We've made the source code available via Github here After the takedown of Cryptolocker, we hav
Threat Spotlight: Upatre - Say No to Drones, Say Yes to Malware
Talos has observed an explosion of malicious downloaders in 2015 which we’ve documented on several occasions on our blog. These downloaders provide a method for attackers to push different types of malware to endpoint systems easily and effectively. Upatre is an example of a mali